Web3, based on blockchain technology, is driving the next generation of technological revolution. More and more people are beginning to participate in this wave of cryptocurrency, but Web3 and Web2 are two entirely different worlds. The Web3 world is a dark forest filled with various opportunities and dangers. In the Web3 world, we witness many people becoming wealthy overnight and achieving financial freedom, while others go bankrupt and struggle to recover. We feel the rapid pace of innovation in this industry. Wallets serve as the entry point and passport into the Web3 world. Understanding wallets can not only help you navigate freely in the Web3 world but also better protect your asset security in this dark forest.
Authors: @SpinachSpinach, @Amber Yang, @Patrick, @Robert Mao, @DJ Qian, @Raymond Qu, @Li Long, @TokenPocket @Roykay @MVP
The article only represents the personal views of the authors and does not constitute any investment advice.
Table of Contents
1. Wallets — The Gateway from Web2 to Web3
(1) What is a wallet? How to understand wallets?
(2) What is the significance of wallet products in the Web3 world?
(3) What would the Web3 world look like without wallet products?
2. The Evolution of Wallets — From Ledger to Public Chain Service Platform
(1) Wallet 1.0 Era — The Accounting Era (2009-2013)
(2) Wallet 2.0 Era — The Smart Contract Era (2014-2018)
(3) Wallet 3.0 Era — The Multi-Scenario Era (2018-Present)
3. A Simple Understanding of Cryptography — The Art of Wallet Generation
(1) How is a wallet generated? How to "log in" to a wallet?
(2) Can private keys be brute-forced?
(3) Private keys are so hard to remember; is there a solution?
4. The Access Tool of the Crypto World — What Can Wallets Do?
(1) Wallets enable asset visualization and private key management.
(2) Wallets facilitate interaction with blockchain applications.
(3) Wallets establish a new paradigm for identity verification.
5. Ensuring Asset Security — How to Choose a Wallet?
(1) Custodial wallets vs. non-custodial wallets — Is the private key in your hands?
(2) Cold wallets vs. hot wallets — Is your private key really safe?
(3) Why are the least secure centralized exchange wallets still the most used?
(4) The crypto world's Lehman moment — How to ensure asset security?
6. The Dark Forest — Unveiling Wallet Scams
(1) Assets transferred directly? — Authorization phishing scams.
(2) Wallet address replaced? — Clipboard virus traps.
(3) Signatures can also be stolen? — eth_sign signature scams.
(4) Free money from the sky? — NFT airdrop scams.
(5) Picking up money in the wallet? — Deliberate private key leak scams.
7. Future Outlook — The Development Trends of Wallets
TL;DR
-
In the Web3 world, wallets not only manage assets in the traditional sense but also serve as essential tools for interaction with blockchain. Without a wallet, it's like not having a health code; you cannot enter the Web3 world.
-
At the beginning of Bitcoin's inception, the barrier to using wallets was high. There were no diverse wallet products available, and users had to download the entire Bitcoin ledger, which took several days. On June 29, 2011, Bitcoin payment processor BitPay launched the first Bitcoin electronic wallet for smartphones, marking the beginning of the mobile wallet era. People no longer needed to learn complex computer knowledge or run large blockchain nodes to use wallets.
-
According to a 2022 survey, there are even 1.7 billion people worldwide without bank accounts, excluded from the global financial system. Wallets can provide these individuals with blockchain-based "bank accounts" and access to financial services without barriers, granting everyone equal access to financial services.
-
If the barrier to using wallets cannot be lowered to a level where everyone can easily use them, Web3 will struggle to become mainstream. Even with endless innovative applications, without a sufficient user base, survival is difficult. It can be said that without wallet products to lower the usage threshold, the foundation for the development of the Web3 world is unstable. The Web3 world needs more users to foster positive development, which is an important significance of wallet products.
-
In the early years of Bitcoin, wallets only had simple transfer and accounting functions. After the birth of Ethereum, wallets entered the smart contract era, allowing interaction with smart contracts in addition to basic transfer and accounting functions. More and more people began to join the blockchain world, but they discovered a problem with Ethereum: congestion, leading to high gas fees and long wait times, prompting the emergence of many high-performance public chains. Thus, wallets entered the multi-scenario era, supporting multiple blockchains and managing different assets across chains simultaneously.
-
When we generate a wallet, we actually create a private key through a series of algorithms, and this private key generates a public key, forming a key pair and a wallet address. Since this process is one-way, holding the private key equates to having control over the wallet. If the private key = wallet account password, then the wallet address is what others need to transfer funds to you. You can make your wallet address public, but you must not disclose your private key, as the private key = wallet control, making its safekeeping especially important.
-
The probability of cracking a Bitcoin address's private key is one in 2 to the power of 256. Even assuming a computer can calculate 9 million possible private keys per second, it would take thousands of years to crack a private key, making brute-forcing nearly impossible with current human computational power.
-
Since private keys appear random and are hard to remember, "mnemonic phrases" were introduced to solve this problem. Mnemonic phrases typically consist of 12 or 24 English words, and they map to the wallet's private key. They can be understood as another representation of the private key, easier to record, and entering the mnemonic phrase can also "log in" to the wallet.
-
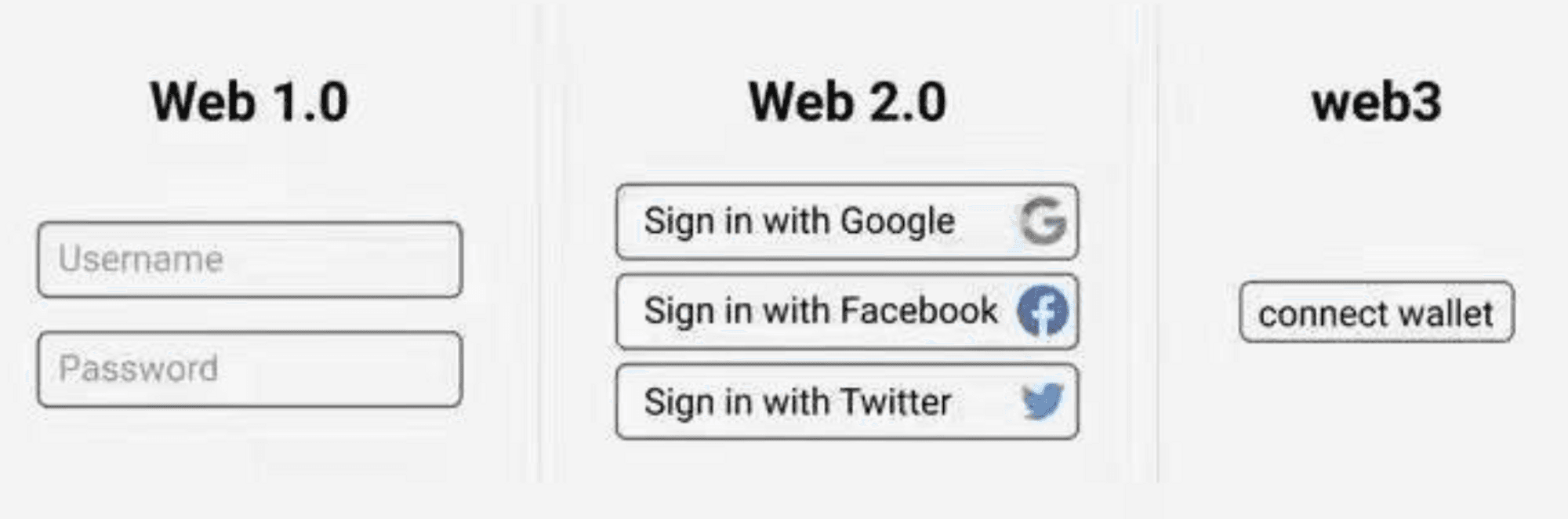
In the Web2 world, accounts between applications are not fully interoperable, but in the Web3 world, all applications use wallets for "login." We can see that when "logging in" to a wallet, it displays "Connect Wallet" instead of "Login with Wallet," and the wallet is your only passport in the Web3 world.
-
Wallets are not just carriers of crypto assets; they also visualize crypto assets and manage private keys — essentially, all our crypto assets are just a string of data on the blockchain. So when you process assets in your wallet (receiving, transferring, paying, etc.), the wallet is essentially managing private keys to visualize and handle crypto asset data.
-
The essence of wallets in the Web3 world lies in experiencing applications on the blockchain, known as DAPPs, typically composed of smart contracts. The blockchain does not stop running, and neither do DAPPs. Wallet interactions with DAPPs usually fall into two categories: identity verification (signatures) and smart contract interactions. The difference between the two is simple: signature authorization is an off-chain interaction that does not require gas fees, while smart contract interactions are on-chain interactions that do incur gas fees.
-
In the Web3 world, wallets can not only store your crypto assets but also grant users ownership, control, and management of decentralized identities, freeing them from reliance on centralized authorities for identity verification, utilizing blockchain technology for identity verification.
-
Regarding the ownership of private keys, three types of wallets have emerged: custodial wallets, hybrid custodial wallets, and non-custodial wallets, where private keys are held by: the user, both the user and the application service provider, or the custodial service provider. Custodial and non-custodial wallets align more closely with Web2 user habits, having a low barrier to entry, but when storing large amounts of assets, non-custodial wallets are a safer and better choice, as having the private key in your hands is the most reassuring.
-
The difference between cold wallets and hot wallets lies in whether the private key is connected to the internet. Even if the private key is in your hands, it is not absolutely secure; you shouldn't put all your eggs in one basket. A seasoned Web3 user typically has multiple wallets to diversify risk, storing most funds in cold wallets and a small amount in hot wallets for convenience.
-
Centralized exchange wallets are actually the least secure type of wallet, yet they are the most used. This phenomenon is due to the irreplaceability of centralized exchanges and the general lack of understanding about wallets among most people.
-
Due to the anonymity of blockchain and the high cognitive barrier, many wallet users lack knowledge about wallet security and the logic of on-chain interactions. This has led to frequent security incidents resulting in significant financial losses, and the chances of recovering stolen funds are slim. It can be said that the crypto world is a dark forest, and to protect your asset security, you must establish an understanding of wallet security.
-
Digital wallets are transitioning from tools used primarily by geeks or cryptocurrency enthusiasts to common products for ordinary users on mobile devices or browsers. This development pattern is consistent with the evolution of internet tools. As wallets integrate with various applications, they are increasingly becoming a strategic entry point into Web3, rather than just a basic tool for managing private keys and digital assets.
1. Wallets — The Gateway from Web2 to Web3#
(1) What is a wallet? How to understand wallets?
A wallet (Crypto Wallet) is commonly referred to as a crypto wallet, digital wallet, or electronic wallet. Why is a wallet considered the gateway to the Web3 world? We cannot use the traditional understanding of wallets to comprehend Web3 wallets. In the Web3 world, wallets not only manage assets in the traditional sense but also serve as essential tools for interaction with blockchain, carrying the mission of human interaction with blockchain. It can be said that without a wallet, it's like not having a health code; you cannot enter the Web3 world.
For users encountering blockchain for the first time, we can initially compare wallets to "Alipay" in a non-strict sense. In the Alipay app, you can perform operations such as payments, transfers, and asset viewing, and you can also use Alipay to log in to third-party apps or websites, even for socializing and chatting. Similarly, wallets in the Web3 world have similar functions and services, but they differ significantly from Alipay, such as:
-
You can register a wallet for free without using an ID card or phone number; wallets are anonymous.
-
Alipay is a company product that can be manipulated, while wallets are native to blockchain and are almost impossible to manipulate.
-
Assets in Alipay are just digital, while assets in wallets truly belong to you.
-
If you forget your Alipay account password, you can recover it; if you lose your wallet's private key (which can be understood as a password), it cannot be recovered.
(2) What is the significance of wallet products in the Web3 world?
The emergence of wallet products in the Web3 world is irreplaceable, as it lowers the barrier for people to use wallets, enabling more individuals to participate in the blockchain world. At the beginning of Bitcoin's inception, the barrier to using wallets was high. There were no diverse wallet products available, and the initial wallet forms were rudimentary, requiring several days to sync and download the entire Bitcoin ledger to operate. Only a few geeks could use wallets on their computers.
(The image below shows the world's first Bitcoin wallet designed by Bitcoin's creator, Satoshi Nakamoto.)
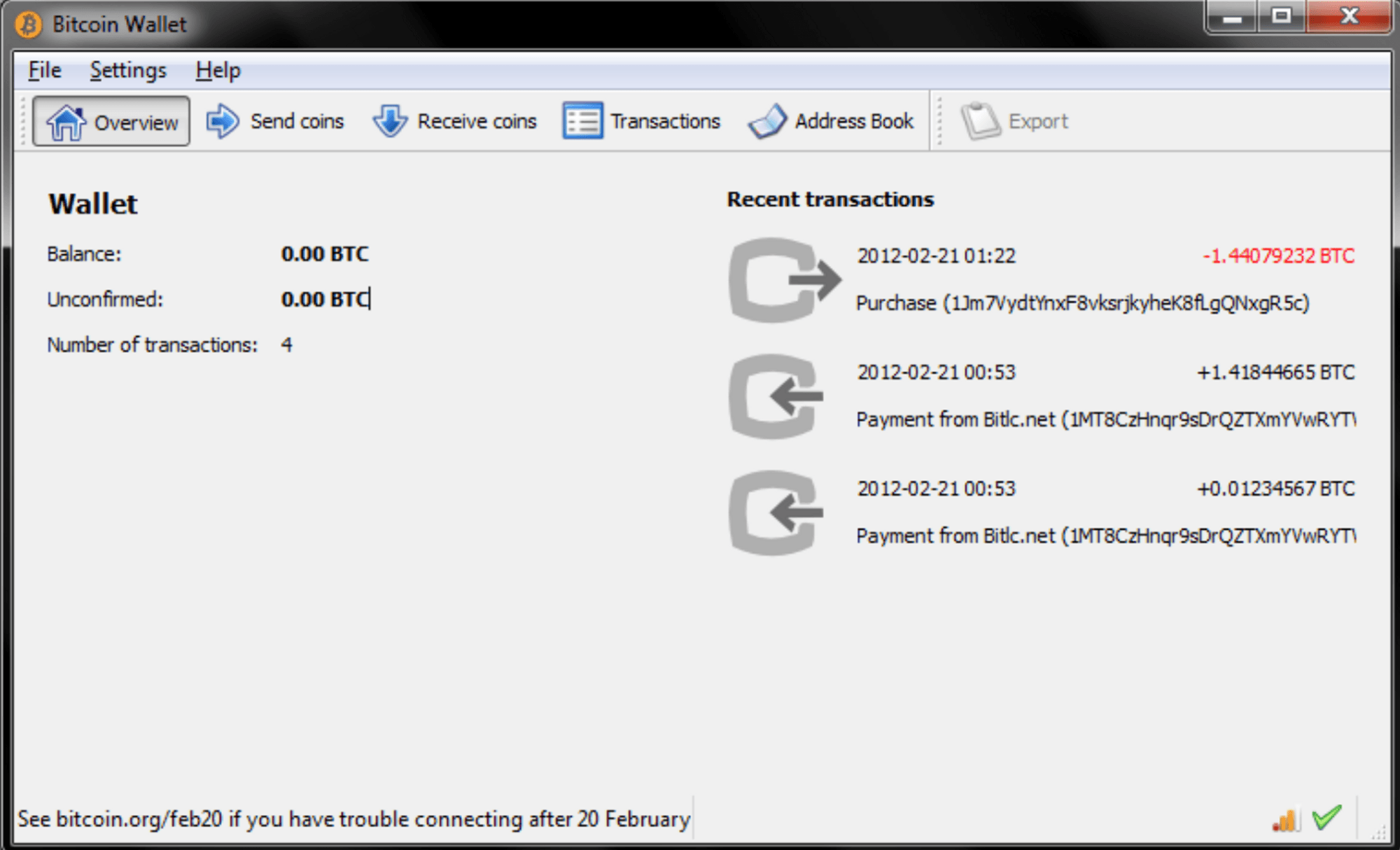
With the development of Bitcoin, on June 29, 2011, Bitcoin payment processor BitPay launched the first Bitcoin electronic wallet for smartphones. Since then, wallets have entered the mobile era, and people no longer need to learn complex computer knowledge or run large blockchain nodes to use wallets. This was a historic step for wallets to reach the masses. Wallet products have continuously iterated and lowered barriers, attracting more users into the blockchain world. What will this bring to the Web3 world?
According to a 2022 survey, there are even 1.7 billion people worldwide without bank accounts, excluded from the global financial system. Wallets can provide these individuals with blockchain-based "bank accounts" and access to financial services without barriers. Wallets not only grant everyone equal access to financial services but also as the barriers to wallet usage decrease, more people will enter the Web3 world. This will bring deeper liquidity and more users to the Web3 world, leading to a more prosperous ecosystem, creating a positive cycle.
(3) What would the Web3 world look like without wallet products?
Let’s review the history of computers. The first electronic computer was born on February 14, 1946, at the University of Pennsylvania, known as "ENIAC." It was invented for missile trajectory calculations. We can see that the initial form of computers was extremely large and complex, accessible only to a small number of people. As time progressed, in December 1974, computer enthusiast Edward Roberts released the "Altair 8800," the first computer equipped with a microprocessor, marking the beginning of personal computers.
The barrier to using computers dropped from being accessible to only a few to being usable by individuals, but this took a long time to develop. With continuous iterations of hardware and operating systems, the transition from a few users to the general public being able to easily use computers occurred. The lowering of barriers led to explosive user growth and the emergence of various applications, such as social platforms, computer games, and office applications, changing human lifestyles.
(The world's first electronic computer)
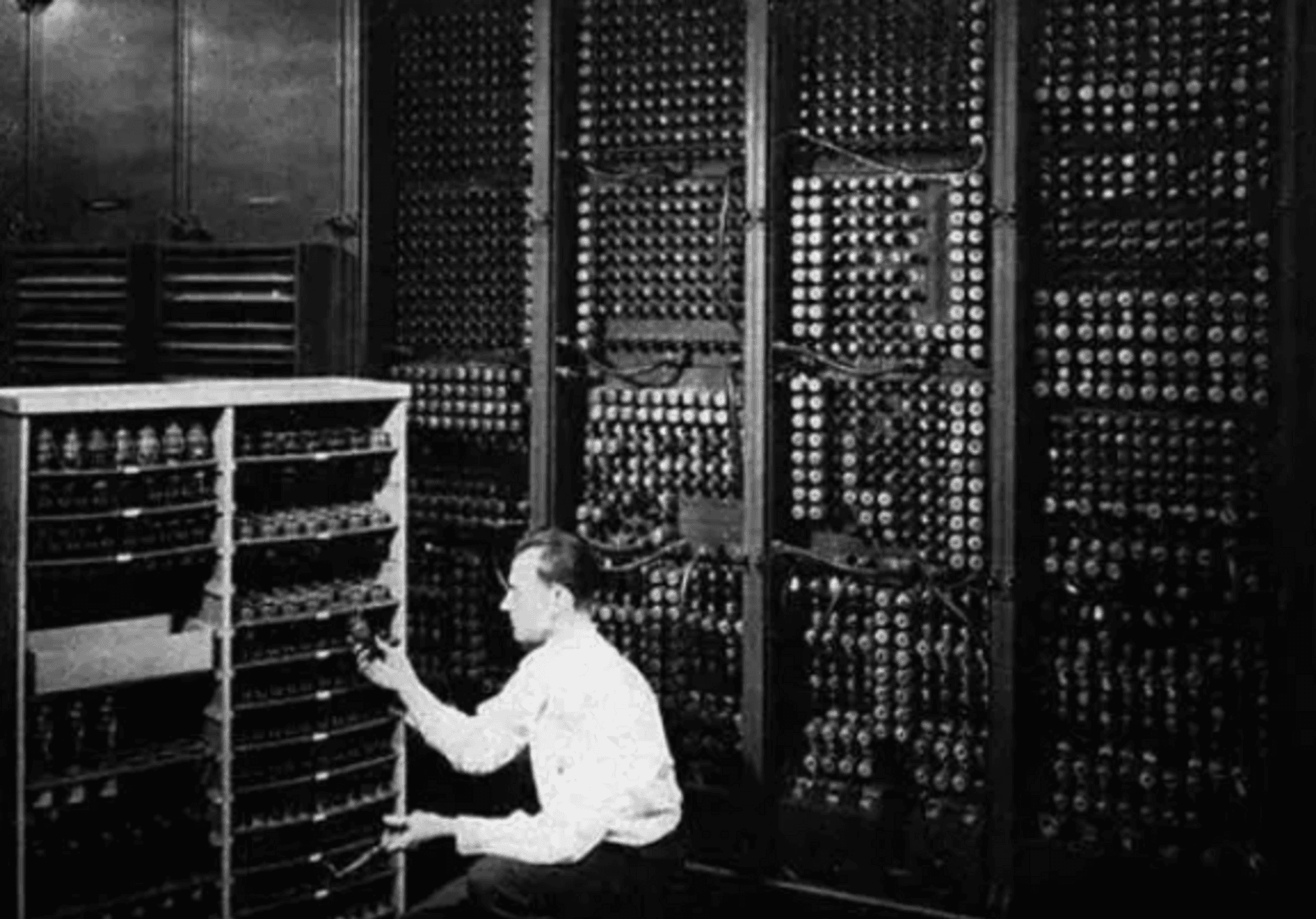
Imagine if computers were still large, complex, and expensive like before; would there be such a rich ecosystem today? The same applies to the Web3 world. If the barrier to using wallets cannot be lowered to a level where everyone can easily use them, Web3 will struggle to become mainstream. Even with endless innovative applications, survival is difficult without a sufficient user base. It can be said that without wallet products to lower the usage threshold, the foundation for the development of the Web3 world is unstable. The Web3 world needs more users to foster positive development, which is an important significance of wallet products.
2. The Evolution of Wallets — From Ledger to Public Chain Service Platform#
The history of wallets dates back to the inception of Bitcoin, when blockchain was merely a distributed ledger. However, with the development of blockchain, wallets have undergone several updates and iterations.
(1) Wallet 1.0 Era — The Accounting Era (2009-2013)
In 2008, Satoshi Nakamoto published a white paper that sparked a global fintech revolution: "Bitcoin: A Peer-to-Peer Electronic Cash System." In 2009, the first crypto asset, Bitcoin, went live on its mainnet, marking the official operation of the first blockchain system. With the launch of the Bitcoin mainnet, Satoshi also developed the first Bitcoin wallet, which only had simple transfer and accounting functions at that time.

(2) Wallet 2.0 Era — The Smart Contract Era (2014-2018)
In 2014, Vitalik Buterin, commonly known as "V God," published a white paper that opened the blockchain 2.0 era: "Ethereum: A Next-Generation Smart Contract and Decentralized Application Platform." Blockchain officially entered the smart contract era. Unlike Bitcoin's distributed ledger, Ethereum allows not only transfers and accounting but also the building of decentralized applications through smart contracts. So, what is a smart contract?
A smart contract can be understood as a program that automatically runs on the blockchain when conditions are met. Once deployed, it runs continuously on the blockchain and cannot be altered. The emergence of smart contracts attracted a large number of developers to Ethereum, bringing many disruptive innovations to blockchain, such as NFTs, decentralized finance on the blockchain, and metaverse games. However, it also led to a chaotic period, as smart contracts allowed anyone to issue their own tokens, and many people had insufficient understanding of blockchain, resulting in various "air coins" that drained many people's pockets, significantly damaging the public's perception of blockchain.
With the advent of smart contracts, wallets underwent an upgrade. The role of wallets evolved from simple transfers and accounting to interacting with smart contracts, marking the entry into the 2.0 era.

(3) Wallet 3.0 Era — The Multi-Scenario Era (2018-Present)
With the birth of Ethereum and smart contracts, more and more people began to join the blockchain world. However, they discovered a problem with Ethereum: congestion. As the number of users increased, Ethereum's processing speed did not change, leading to high gas fees and long wait times. Gas fees can be simply understood as tips paid to miners, as transactions on the blockchain require miners to record them. You need to pay miners to process your transactions. If a large number of transactions pile up at the same time, congestion occurs, and miners prioritize processing transactions based on who pays them more. This can lead to gas fees of hundreds or even thousands of dollars for a single transaction or processing times exceeding half an hour, which is unacceptable for ordinary users.
During this period, many so-called high-performance and highly scalable new public chains and second-layer blockchains (Layer 2) emerged to address Ethereum's congestion issues. This initiated a competitive era of multi-chain ecosystems, with each chain having its own dedicated wallet. Wallets entered the 3.0 era, the multi-scenario era, where single-chain exclusive wallets gradually declined. From a consumer perspective, no one wants to install a different wallet for each chain, as this increases wallet management costs.
Wallets began to evolve into public chain service platforms, as single-chain solutions could no longer meet user needs. Wallets started supporting multiple blockchains and managing different assets across chains simultaneously, while also continuously improving user experience. Nowadays, users can perform cross-chain asset transactions, interact with smart contracts, socialize, access information, and check market trends all within their wallets.
3. A Simple Understanding of Cryptography — The Art of Wallet Generation#
(1) How is a wallet generated? How to "log in" to a wallet?
After understanding the significance and history of wallets, you may wonder about the mechanism behind wallet generation. Wallets do not require identity information like traditional registered accounts and are anonymous, allowing true ownership of assets. How is this achieved? The answer lies in cryptography.
If you are a beginner, seeing cryptographic terms like hash functions, elliptic curve encryption algorithms, private keys, public keys, and asymmetric encryption might overwhelm you. This section will not delve into the complex knowledge of cryptography but will simply explain the key principles behind wallet generation.
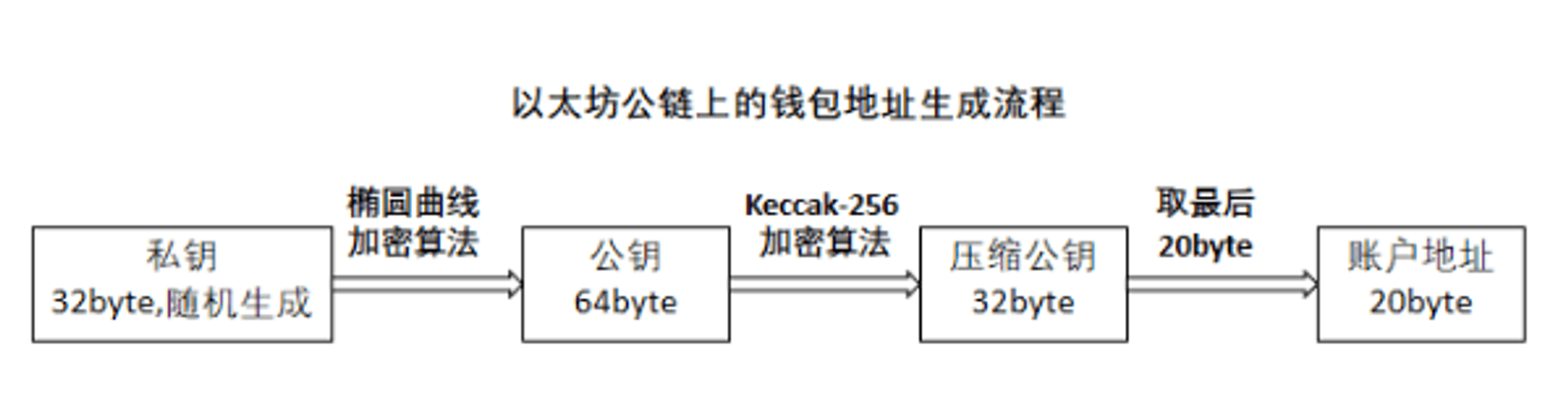
First, a crucial cryptographic term to remember is the private key (Private Key), which can be understood as the wallet's account password. When we generate a wallet, we actually create a private key through a series of algorithms, and this private key generates a public key, forming a key pair and a wallet address. Since this process is one-way, holding the private key equates to having control over the wallet.
If the private key = wallet account password, then the wallet address is what others need to transfer funds to you. You can make your wallet address public, but you must not disclose your private key. Because the private key = wallet control, its safekeeping is especially important. You can use the private key anywhere to recover your wallet; unlike traditional account passwords, you can "log in" to the wallet by simply entering the private key.
(Ethereum public chain wallet generation process)
(2) Can private keys be brute-forced?
A wallet can be "logged in" with just one private key, unlike traditional accounts that require both an account and a password. You might wonder, "What if someone brute-forces the private key to log into someone else's wallet?" Rest assured, if this were possible, Bitcoin would have likely already collapsed. The private key of Bitcoin consists of a 256-bit binary array (like 0101010101), and the probability of cracking a Bitcoin address's private key is one in 2 to the power of 256. Even assuming a computer can calculate 9 million possible private keys per second, cracking a private key would take thousands of years, making brute-forcing nearly impossible with current human computational power. Even with the advent of quantum computers, due to different algorithms and the emergence of quantum-resistant technologies, we need not worry about the security of private keys.
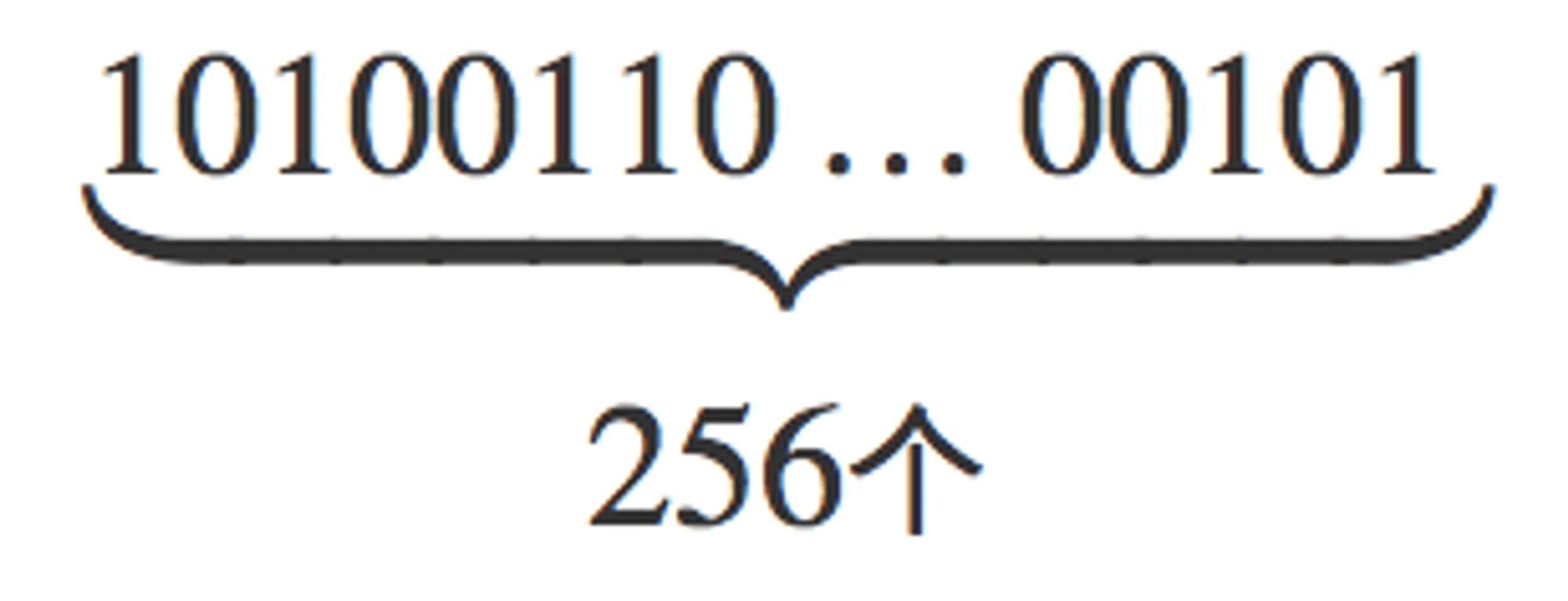
(3) Private keys are so hard to remember; is there a solution?
Now that we understand private key = wallet control, private keys appear as a random string of characters. Even writing them down on paper can lead to errors, let alone memorizing them. To solve this problem, we introduced a new concept: mnemonic phrases.
Mnemonic phrases typically consist of 12 or 24 English words. Mnemonic phrases map to the wallet's private key and can be understood as another representation of the private key, easier to record. Entering the mnemonic phrase can also "log in" to the wallet. Therefore, both mnemonic phrases and private keys need to be safeguarded and kept secret; otherwise, others can easily access your assets from your wallet.
(Example of a mnemonic phrase)
(4) Wallets are the Only Passport in the Web3 World
As you explore various blockchain-related applications and websites through your wallet in the Web3 world, you will notice that every application on a public chain uses wallets for "login." This differs from our traditional understanding of "login." In the Web2 world, accounts between applications are not fully interoperable. For example, you cannot use your QQ Speed account to log into KartRider, nor can you use your WeChat account to log into Twitter; there is no unified account password to log into all applications. However, in the Web3 world, all applications uniformly use wallets for "login." We can see that when "logging in" to a wallet, it displays "Connect Wallet" instead of "Login with Wallet." The wallet is your only passport in the Web3 world.
4. The Access Tool of the Crypto World — What Can Wallets Do?#
As the access tool of the crypto world, wallets serve not only to transfer and receive funds but also to store and manage private keys, visualize crypto assets, verify identities, interact with smart contracts, and even facilitate social interactions. How should we understand these concepts and perform practical operations?
(1) Wallets Enable Asset Visualization and Private Key Management
Many people entering the Web3 world often start by purchasing crypto assets. Wallets are not only carriers of these assets but also visualize crypto assets and manage private keys. Essentially, all our crypto assets are just a string of data on the blockchain. So when you process assets in your wallet (receiving, sending, paying, etc.), the wallet is essentially managing private keys to visualize and handle crypto asset data.
In the image below, we can see the interface displayed to users in the Metamask wallet:
- The wallet address, which is your receiving account; to transfer crypto assets into it, you need this address.
- Common asset operation shortcut buttons: Receive, Buy, Send, Swap; the wallet's basic functions are all here.
- The asset list, where all your crypto assets are displayed, and you can click on any asset to view transaction details.
So once we generate a wallet, we can withdraw assets from exchanges by entering the wallet address to transfer assets into the wallet or directly use third-party services within the wallet to purchase crypto assets. After that, you can see and manage your crypto assets in the wallet, with basic functions for transferring and exchanging other crypto assets readily available on the interface. Congratulations, you have learned the basic usage of a wallet.

(2) Wallets Facilitate Interaction with Blockchain Applications
Of course, learning the basic usage of wallets is far from enough. The essence of wallets in the Web3 world lies in experiencing applications on the blockchain, which we commonly refer to as DAPPs. How do they differ from the mobile apps we usually use? The simple distinction is that apps run on centralized servers and can be stopped or modified at any time. In contrast, DAPPs run on decentralized blockchains and are typically composed of smart contracts; as long as the blockchain operates, DAPPs will not stop running.
What are the ways wallets interact with the blockchain?
Wallet interactions with DAPPs typically fall into two categories: identity verification (signatures) and smart contract interactions. Signature authorization is an off-chain interaction that does not require gas fees, while smart contract interactions are on-chain interactions that do incur gas fees. In what scenarios would different interaction methods be used?
For example, if you want to sell your NFT on Opensea (currently the largest NFT marketplace), Opensea will request a signature (identity verification) from you to prove you are the holder of the private key. Once sent, your NFT will be listed for sale on the market. Your NFT is still in your wallet, and there is no transfer of assets involved — meaning no changes to the blockchain data, so there are no gas fees to pay. If during this time someone wants to buy your NFT and places an order on Opensea, the buyer will need to pay a gas fee in addition to the NFT price. Why? Because purchasing your listed NFT involves transferring it from your wallet to the buyer's wallet, which is an interaction with the smart contract, requiring miners to facilitate the NFT asset transfer, hence the gas fee.
(The images below show the signature interface for the seller and the smart contract interaction interface for the buyer.)
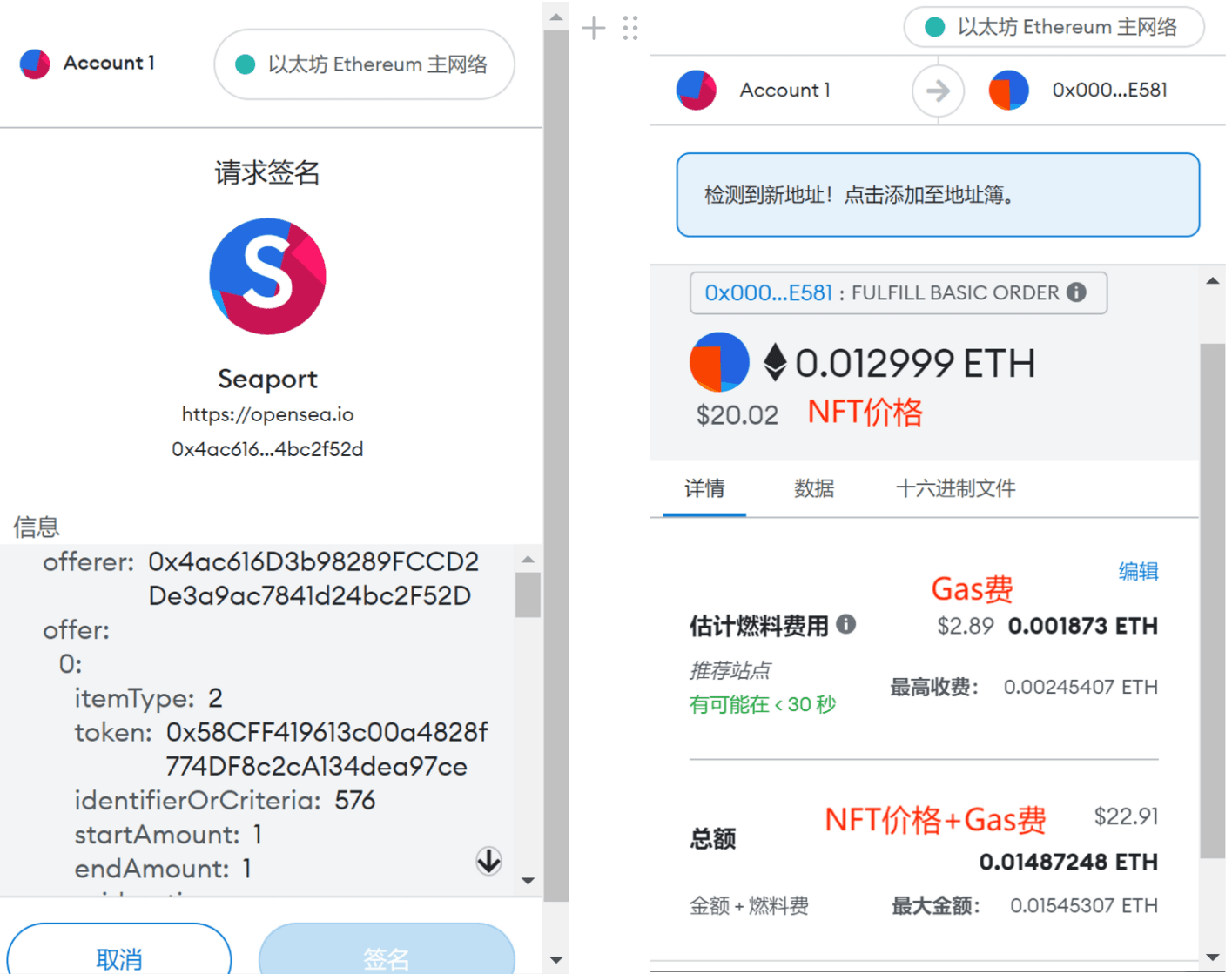
(3) Wallets Establish a New Paradigm for Identity Verification
Let's conduct an experiment. If you are carrying your traditional wallet, please take it out and see what you have inside. Perhaps cash, or some credit or debit cards, but you might also have your ID card, driver's license, or insurance card in there! Typically, our traditional wallets are not only used to hold money and make payments but also to store our identity documents.
In the Web3 world, wallets can not only store your cryptocurrencies but also "hold identity documents" and establish identity verification. Why do we say wallets establish a new paradigm for identity verification? We first need to understand the difference between traditional identity verification and identity verification in the Web3 world.
In real life, our identities are generally granted by centralized authoritative institutions. Our national ID cards, passports, and other identification documents are issued by state authorities, and we often rely on these "verifiable existence proofs" for social activities such as healthcare, financial services, education, and travel, and our identity information is often stored in centralized databases, which poses risks of leakage and tampering.
In the Web3 world, decentralized identities allow users to have ownership, control, and management of their identities, freeing them from reliance on centralized authorities for identity verification, utilizing blockchain technology for identity verification. Since everyone is anonymous in the Web3 world, this anonymity can lead to issues like witch hunts, so the on-chain identity system brings a new "social relationship" to the Web3 world.
The identity forms existing on the blockchain are not limited to traditional identity information. On-chain identities can be certifications of real-world identities or identity verifications based on on-chain behavior, such as contributions recognized in DAOs. All identity verifications can be completed using wallets, providing wallets with more imaginative possibilities.
The Soul Bound Token (SBT) proposed by Ethereum founder Vitalik has been frequently mentioned in this wave of digital identity development, with many different implementations. SBT uses non-transferable NFTs as carriers to achieve a certain degree of on-chain identity management. However, SBT still lacks unified standards and practical usage protocols, and its development prospects remain to be seen.
ArcBlock's DID Wallet is the first product on the market that combines a blockchain digital asset wallet with a DID digital identity wallet. ArcBlock's DID Wallet is also a digital identity wallet that supports W3C DID (a decentralized identity standard) and is compatible with Ethereum, various Ethereum-compatible chains and Layer 2, Solana chain, and ArcBlock chain. The DID Wallet can support NFT standards across chains, thus supporting SBTs implemented based on NFTs. Most digital asset wallets that support Ethereum NFTs can also manage user identities based on NFTs and various "DID track" projects implemented with NFTs.
Currently, the development of decentralized identity systems is still in its early stages, with many issues yet to be resolved. However, with the development of decentralized identities, we believe that wallets, as carriers of identity in the Web3 world, will bring about a new paradigm for identity verification in the future.
5. Ensuring Asset Security — How to Choose a Wallet?#
There are many types of wallets, which can be categorized based on whether they are connected to the internet, the ownership of private keys, the degree of decentralization of the network, the method of private key generation, and the type of wallet account.
If we focus solely on asset security, how should we choose a wallet?
(1) Custodial Wallets vs. Non-Custodial Wallets — Is the Private Key in Your Hands?
Why is it important to distinguish between custodial and non-custodial wallets? Because this determines whether you hold the wallet's private key, in other words, whether the wallet truly belongs to you. How do we differentiate?
Regarding the ownership of private keys, three types of wallets have emerged: custodial wallets, hybrid custodial wallets, and non-custodial wallets.
Non-Custodial Wallets:
The wallet's private key is held by the user, who has full ownership of the wallet. The barrier to entry is higher, but security is the highest. Users must properly safeguard their wallet's private key/mnemonic phrase, as losing it means it cannot be recovered. Wallets that can be generated and "logged in" only through private key/mnemonic phrase are typically referred to as non-custodial wallets.
Hybrid Custodial Wallets:
The wallet's private key is held by both the user and the application service provider. This type is commonly used by low-barrier wallet products, where both parties hold the private key and use technologies like two-factor authentication (2FA) to ensure wallet asset security. The barrier to entry is lower, recovery is possible if lost, and security is between custodial and non-custodial wallets.
Custodial Wallets:
The wallet's private key is held by a third-party custodial institution, meaning the user only has usage rights, not ownership. The barrier to entry is lower, and the wallet can be recovered. Assets are merely displayed as numbers, and custodial institutions can arbitrarily misuse user funds. Centralized exchange wallets are the most common type of custodial wallets.
If you are a newcomer to the Web3 world or prefer a more convenient user experience, custodial or hybrid custodial wallets may be more suitable for you. Custodial and hybrid custodial wallets align closely with Web2 user habits: using account passwords to log in, not needing to safeguard private keys or mnemonic phrases, and being able to recover forgotten passwords. If you want a wallet with higher security that you fully control, especially when storing large amounts of assets, then a non-custodial wallet is the best choice, as having the private key in your hands is often the most reassuring.

Common non-custodial wallets: TokenPocket, OneKey, BitKeep
Common hybrid custodial wallets: Blockchain, Zengo
Common custodial wallets: Binance, Huobi
(2) Cold Wallets vs. Hot Wallets — Is Your Private Key Really Safe?
First, let me ask you a question: Is having the private key in your hands absolutely safe? Let me share a true story. A hacker group once infiltrated the network of the Colonial Pipeline Company in the U.S. and demanded Bitcoin as ransom. In the end, the hacker group successfully obtained 75 Bitcoins, and later the FBI managed to recover 63.7 Bitcoins from the hacker's wallet. If the uninformed public hears this, they might think, "What!! Bitcoin can be recovered? Isn't Bitcoin anonymous? It seems Bitcoin is unreliable and a scam!"
If you think this way, you are mistaken. The reason the FBI could recover the ransom from the hacker was not due to an issue with Bitcoin itself, but because the hacker stored the wallet's control, i.e., the private key, on a computer connected to the internet. The FBI hacked into the hacker's computer and obtained the private key, allowing them to easily recover the Bitcoins from the hacker's wallet.
So, what do cold wallets and hot wallets have to do with this story? Let’s assume that if the hacker had not stored the private key on a computer connected to the internet but had written it down on a piece of paper, do you think the FBI could have recovered the ransom? The answer is no, unless the FBI directly raided the hacker's home and obtained that piece of paper with the private key. That piece of paper essentially represents a cold wallet. How do we distinguish between cold wallets and hot wallets?
Cold Wallets:
The wallet's private key does not connect to the internet, making it suitable for storing large amounts of funds, with high security that effectively prevents private key leakage. Common forms include: written on paper, memorized, hardware wallet products, or phones/computers that have never connected to the internet.
Hot Wallets:
The wallet's private key is connected to the internet, making it suitable for high-frequency on-chain operations, with high convenience but risks of hacking and theft. Common forms include: web/extension wallets, mobile wallets, desktop wallets, and centralized exchange wallets.
The Web3 world is a dark forest filled with various scams and traps, where users may inadvertently lose all their assets. As the saying goes, you shouldn't put all your eggs in one basket. A seasoned Web3 user typically has multiple wallets to diversify risk, storing most funds in cold wallets and a small amount in hot wallets for convenience.

Common cold wallets: Ballet, Ledger
Common hot wallets: MetaMask, TokenPocket
(3) Why are the least secure centralized exchange wallets still the most used?
After understanding custodial and hot wallets, you will find that centralized exchange wallets are actually the least secure type of wallet. Yet, the least secure wallets are the most used. This phenomenon is due to the irreplaceability of centralized exchanges and the general lack of understanding about wallets among most people.
The significance of centralized exchanges lies in providing a high-efficiency, low-cost trading matching platform for the crypto world, which is currently irreplaceable. Although decentralized exchanges (DEXs) have emerged, for most users unfamiliar with wallet operations, the barrier to entry is high. Moreover, before the advent of decentralized exchanges (DEXs), people could only trade crypto assets through centralized exchanges or over-the-counter transactions.
Over-the-counter trading is a low-efficiency and high-risk trading method. Due to the high volatility of crypto assets, blockchain confirmation wait times, and legal ambiguities, people may encounter many unexpected situations during over-the-counter trading: paying money and the other party running away, waiting a long time for Bitcoin transfers to arrive, needing to renegotiate prices due to drastic price fluctuations during the transaction, being unable to find a trading counterpart, transferring to the wrong account, etc.

The order book trading model of centralized exchanges greatly improves trading efficiency and liquidity, providing users with guaranteed fiat currency deposit and withdrawal services and low-barrier wallet account services. It can be said that without the existence of centralized exchanges, the trading scale of the crypto world would not be as large as it is today.
The convenience and low barriers of centralized exchanges have made them the preferred trading venues for many, attracting a large user base. This has made centralized exchange wallets the most used wallets, while also bringing substantial profits to centralized exchanges. Due to the lack of global regulation and legal frameworks for the entire crypto world, the rampant misuse of user funds by centralized exchanges has begun to emerge.
Many users approach centralized exchanges with a speculative mindset, and many users may not even know what blockchain is. The lack of knowledge about crypto leads many users to be unaware that storing crypto assets in exchanges is unsafe. In fact, the assets displayed in centralized exchange wallets are merely numbers allocated by the exchange, and all assets reside in the centralized exchange's wallet, similar to the balance displayed in a traditional bank account. Due to the arbitrary misuse of user funds by many centralized exchanges, the funds cannot be 100% redeemed. In the event of a crisis leading to a bank run, many users' funds in centralized exchanges may become unrecoverable, causing irreparable losses. Therefore, users need to be cautious about storing large amounts of assets in centralized exchanges.
(4) The Crypto World’s Lehman Moment — How to Ensure Asset Security?
November 2022 is destined to be a month recorded in the history of cryptocurrency, as the crypto world is experiencing the shock brought by the "crypto Lehman moment." Who would have thought that Sam Bankman-Fried (SBF), the founder of the globally second-largest exchange FTX and the multi-billion-dollar crypto hedge fund Alameda Research, who once graced the cover of the famous American magazine Fortune as "the next Buffett," would become the protagonist of this crisis? SBF's business empire collapsed, and from being hailed as the "crypto king," he has now fallen from grace, with his net worth plummeting from $16 billion to $1 in just a few days, as everything seemed to happen too quickly, leaving little time for reaction.

The incident began on November 3, 2022, when Coindesk published a financial document about Alameda Research. The document revealed that Alameda Research held a total of $14.6 billion in assets, including $3.66 billion in "unlocked FTT" and $2.16 billion in "FTT collateral," $292 million in "unlocked SOL," $863 million in "locked SOL," and $41 million in "SOL collateral." Other mentioned tokens included low liquidity project tokens like SRM, MAPS, OXY, and FIDA, along with $134 million in cash and equivalents and $2 billion in stock investments. However, its liabilities reached as high as $8 billion, with $7.4 billion in dollar loans. Where was the problem?
Even those without financial knowledge can spot some clues in this financial document. The FTX platform token FTT occupies a significant portion of Alameda Research's assets, and both Alameda Research and FTX are companies under SBF. It can be said that most of Alameda Research's net assets are tokens "printed" out of thin air by FTX, and Alameda Research used these tokens to secure loans in real dollars. Data from blockchain explorers shows that FTT is highly centralized, with the top three addresses holding 80% of the total supply; once sold, there would be no liquidity in the market. It is precisely this highly concentrated and illiquid FTT that accounts for 88% of Alameda Research's net assets, and if FTT's price drops, Alameda Research would face a liquidity crisis and insolvency.
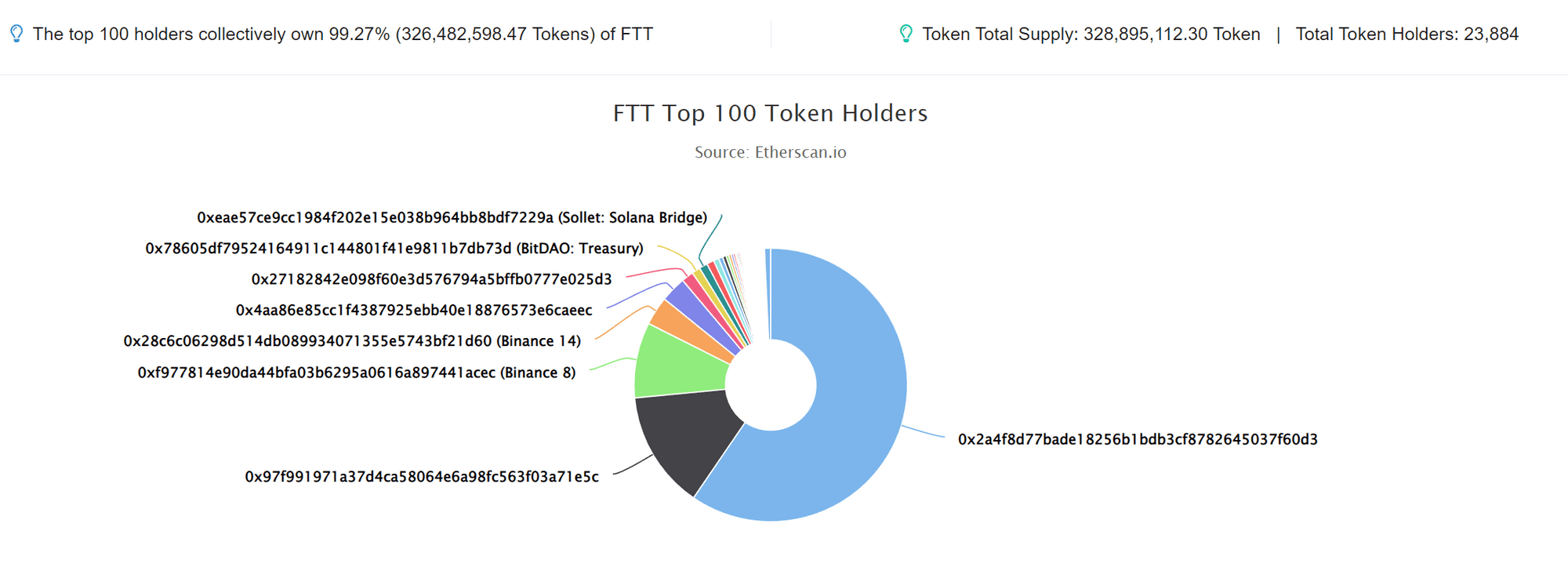
With the publication of this financial document from Alameda Research, discussions began to circulate, raising market concerns. Although Alameda Research claimed to have repaid most of its loans, due to some personal grievances between SBF and Binance founder Changpeng Zhao (which will not be elaborated here), Zhao publicly announced on November 6, 2022, that he would sell all FTT on his books, which triggered a panic in the market.
Despite SBF personally attempting to stabilize user sentiment, it seemed ineffective. A bank run on FTX erupted, with a large number of users continuously withdrawing assets from FTX, resulting in $6 billion in assets being withdrawn within 72 hours. The price of FTT plummeted, and FTX began to become insolvent and stopped accepting withdrawal requests, exposing SBF's "emperor's new clothes."
After FTX became insolvent and stopped accepting withdrawal requests, SBF had no choice but to sell FTX to his competitor Zhao, who began preparing to acquire FTX and signed a letter of intent, sparking intense discussions in the market. However, a reversal occurred when Zhao announced he would abandon the acquisition of FTX, citing the massive funding gap and a series of legal issues. Thus, after a series of small incidents and attempts to save itself, FTX announced bankruptcy on November 11, 2022, with the price of FTT dropping from $25 at the beginning of the month to $1, and the impact of SBF's business empire collapse was just beginning...

Subsequently, it was revealed that FTX had a funding gap of over $8 billion, with the number of creditors potentially reaching 1 million, and the entire crypto market was severely impacted by FTX's collapse. The hardest hit were the users who trusted FTX and the associated companies. For FTX users, many lost all their assets during this crisis, which serves as a wake-up call for all crypto world users: assets need to be in your own hands. Elon Musk also stated in a Twitter Space after FTX's collapse: "Not Your Key, Not Your Wallet." Users need to have their own wallets and store their assets within them, rather than trusting centralized exchanges that may misuse user funds.
The collapse of FTX dealt a serious blow to confidence in the entire Web3 industry; this does not mean the failure of Web3 but certainly signifies the failure of centralized exchanges (CEXs). The impact of FTX is far from over; when will the next crisis occur? No one knows, but we hope that the collapse of FTX can bring better self-regulation to the entire industry and awaken asset security awareness among all Web3 users.
6. The Dark Forest — Unveiling Wallet Scams!#
Due to the anonymity of blockchain and the high cognitive barrier, many wallet users lack knowledge about wallet security and the logic of on-chain interactions, leading to frequent security incidents resulting in significant financial losses. Moreover, the chances of recovering stolen funds are minimal. It can be said that the crypto world is a dark forest, and to protect your asset security, you must establish an understanding of wallet security. Below are some common scams unveiled.
(1) Assets Transferred Directly? — Authorization Phishing Scams
Wallet authorization theft is the most common method of asset loss in wallet cases. Typically, victims click on unknown links (such as airdrops, whitelist claims, etc.) and authorize their assets to scammers without understanding what authorization means, resulting in scammers transferring assets from the victim's wallet. One of the more famous cases involved Jay Chou's NFT worth over 3 million being stolen due to authorization given to a phishing website. How can we understand the principle behind this scam?
When we interact with smart contracts, we are actually interacting with a specific function within the smart contract. The functions can be viewed on blockchain explorers. When we enter a phishing website, we might see a button for Free Mint (free NFT minting). When you click it, you think you can get an NFT for free, but the interaction interface that pops up is actually authorizing your assets to the scammer. If you click and interact, your assets will be stolen.
(The displayed case is an ERC721 standard NFT; the difference from ERC20 fungible tokens is whether authorization changes to the authorized amount.)
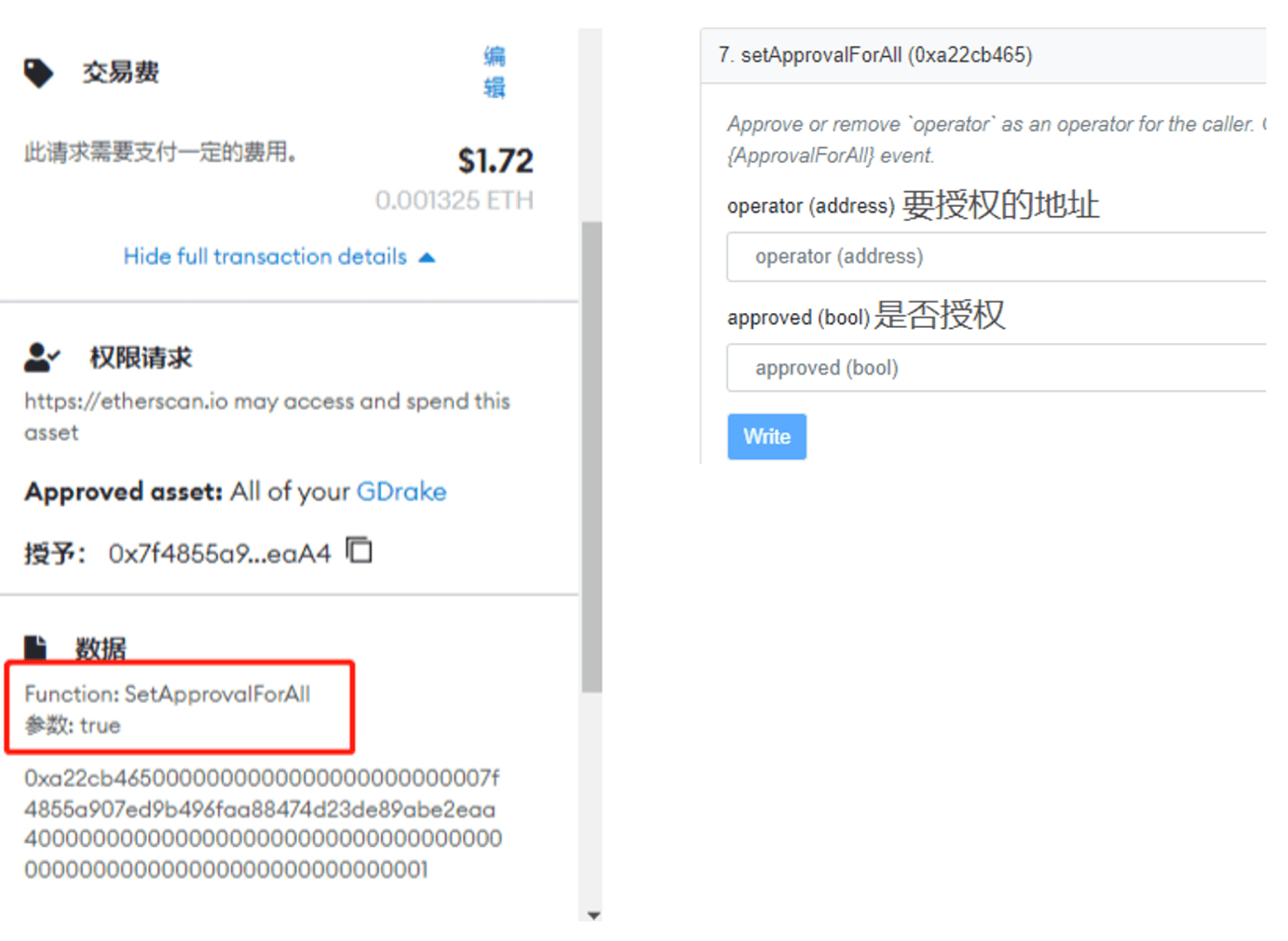
The principle of interaction is that your wallet will send an authorization (Approve) function to the scammer's designated smart contract with specified parameters, essentially authorizing your assets to the scammer's wallet address. Authorization means you allow others to call the smart contract's transferFrom function, allowing scammers to directly transfer the authorized assets from your wallet.
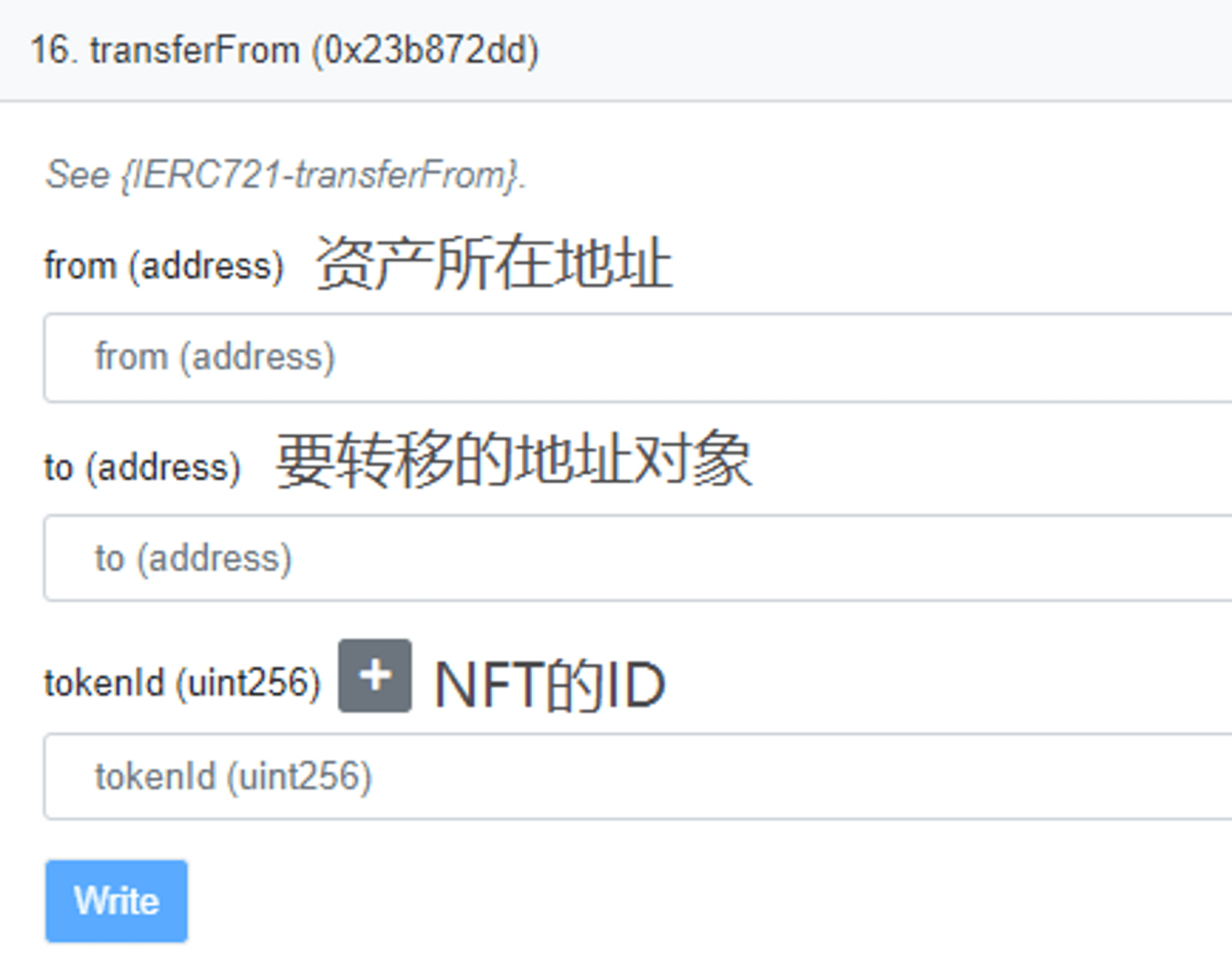
Response strategy: Do not trust any unknown links; if you do not understand the interaction interface, check for the keyword "Approve." Download wallet security plugins, and avoid using wallets containing large amounts of assets for interactions.
(2) Wallet Address Replaced? — Clipboard Virus Traps
Clipboard virus traps are a subtle and pervasive threat, commonly spread on social software like Telegram in Web3. Once you download a file containing a clipboard virus, this virus will lie dormant on your computer, waiting for an opportunity. The virus will automatically recognize wallet address formats and replace the address you should paste with the scammer's address after you copy and paste it. Anyone who does not carefully check the wallet address will fall victim and lose assets.
Example of a file containing a clipboard virus:
Response strategy: Once infected, it is difficult to trace; usually, the only option is to reinstall the system. Do not download files sent by strangers, and most importantly, always verify the wallet address before transferring.
(3) Signatures Can Also Be Stolen? — eth_sign Signature Scams
The eth_sign scam is a phishing method that uses off-chain signature authorization to steal wallet assets, and this scam is more challenging to prevent than on-chain authorization phishing. This is because off-chain signature interactions do not incur gas fees, leading to a lower sense of vigilance among users.
The principle of this scam exploits a signature method in Ethereum called eth_sign. Simply put, it’s like you wrote a "blank check" with your signature for the scammer, and the scammer can write whatever they want on the check. The scammer can then take the signed check to the bank to redeem assets.
The image below shows the format of this signature method; the eth_sign signature format consists of a 32-byte data string, and MetaMask will issue a warning for this signature format, making it relatively easy to identify.
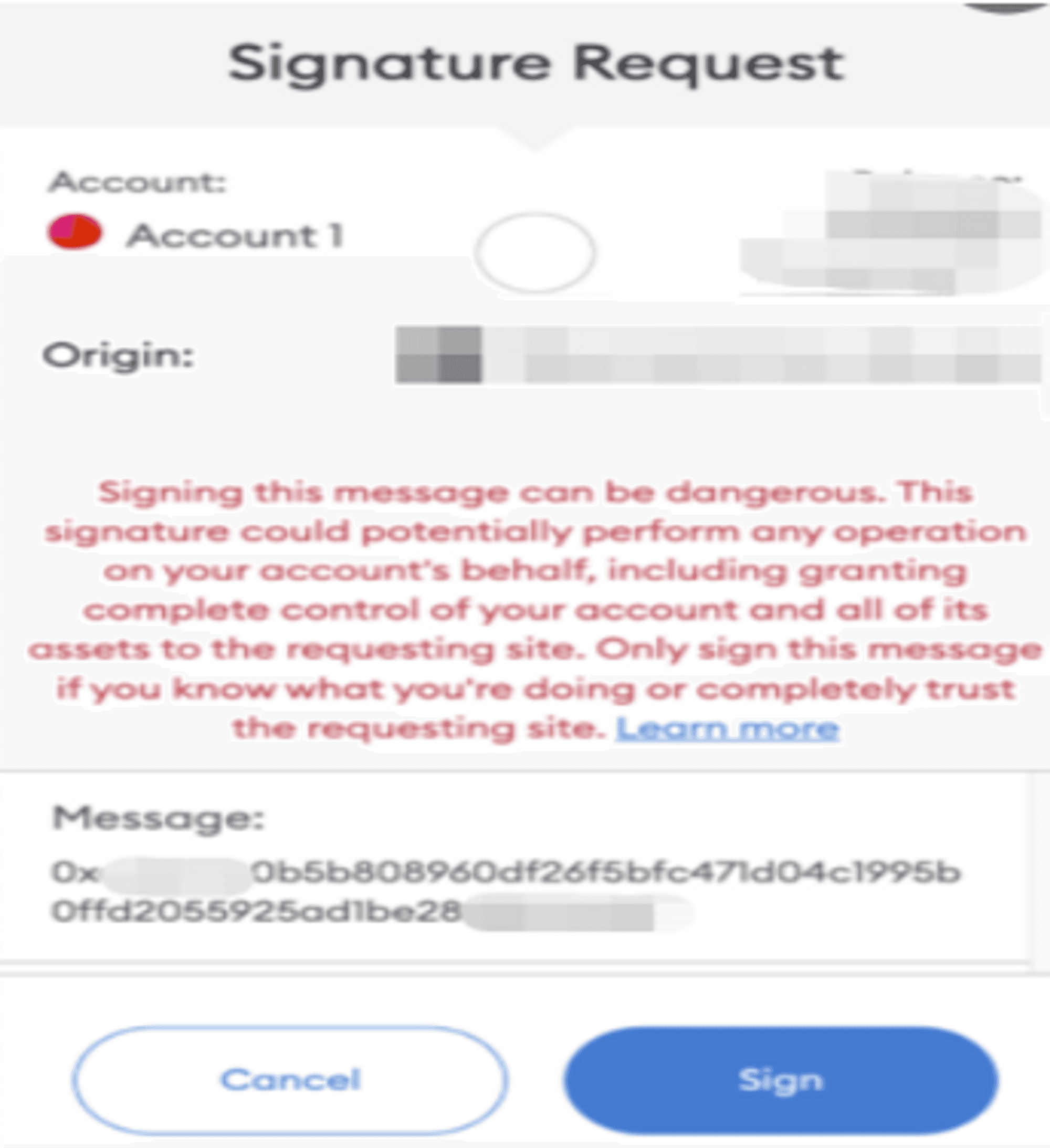
Response strategy: If you see a warning in the interaction interface, be cautious and download wallet security plugins.
(4) Free Money from the Sky? — NFT Airdrop Scams
NFT airdrop scams are a combination of scams. If one day you open an NFT trading platform and see that you suddenly have an additional NFT, and someone has made a high-priced offer to buy this NFT, those who do not understand will surely feel like they have struck gold. However, if you accept the offer, you will find that you cannot sell it.
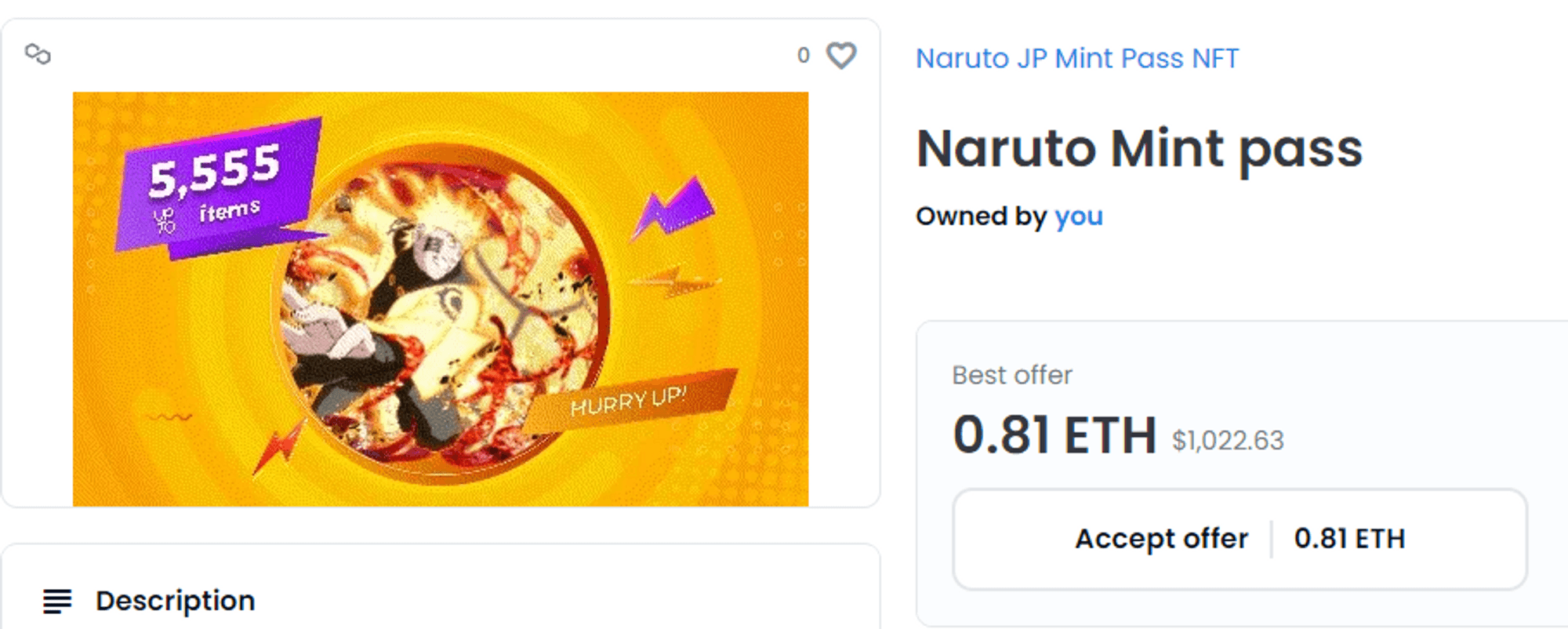
The reason you cannot sell it is that the smart contract for this NFT has disabled the transfer function, meaning this NFT cannot be traded. If you ignore it at this moment, the scam will not deceive you. But if you are tempted by the amount in the offer and enter the NFT's official website through the trading platform, you will find that this is actually a phishing scam, either through authorization or signatures, just with an NFT airdrop and offer as bait.

Response strategy: Do not believe in free money from the sky.
(5) Picking Up Money in the Wallet? — Deliberate Private Key Leak Traps
The deliberate leak of mnemonic phrases/private keys is a scam that exploits people's greed. Scammers will intentionally leak their wallet's mnemonic phrase/private key online. When you enter the mnemonic phrase/private key into the wallet, you will find that the wallet contains some assets but lacks gas fees. If you transfer gas fees into the wallet at this point, you will find that the gas fees disappear the moment they arrive. This is because these wallets typically have many bots monitoring them; once they detect gas fees being transferred in, they will instantly transfer them away. Even if you have gas fees, you will not be able to transfer the assets in the wallet.

The reason the assets cannot be transferred is that these wallets typically contain blacklisted assets, which are assets that have entered the smart contract blacklist. For example, centralized stablecoins like USDT and USDC. Blacklists are often used to assist law enforcement or punish malicious wallets, but not only these centralized stablecoins exist on blacklists. When you are attracted to the assets in the wallet, scammers are also eyeing your gas fees.
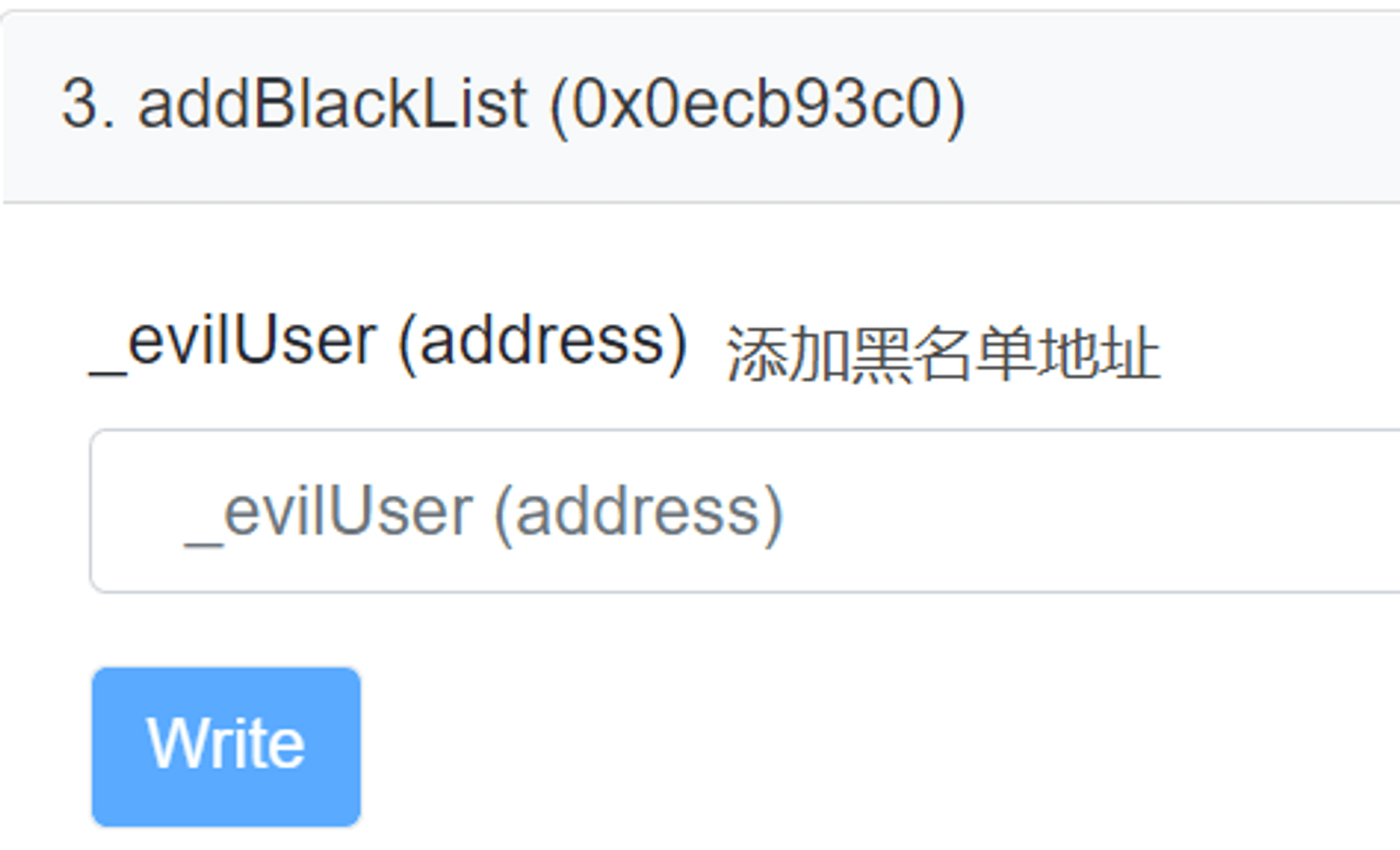
Bonus: The mnemonic phrase image in the section on the art of wallet generation is an example; this wallet has assets on the Tron chain, and you can enter the mnemonic phrase to experience it, but do not transfer money into it!
7. Future Outlook — The Development Trends of Wallets
In this article, we can see that digital wallets are transitioning from tools used primarily by geeks or cryptocurrency enthusiasts to common products for ordinary users on mobile devices or browsers. This development pattern aligns with the evolution of internet tools. As wallets integrate with various applications, wallets are increasingly becoming a strategic entry point into Web3 rather than just a basic tool for managing private keys and digital assets.
In the latest product maturity curve (Hype Cycle) by the renowned IT consulting firm Gartner in 2022, Gartner's analysts classify digital wallets (including those in Decentralized Identity) at the peak of inflated expectations, predicting that they will remain in this position for the next 5-10 years.
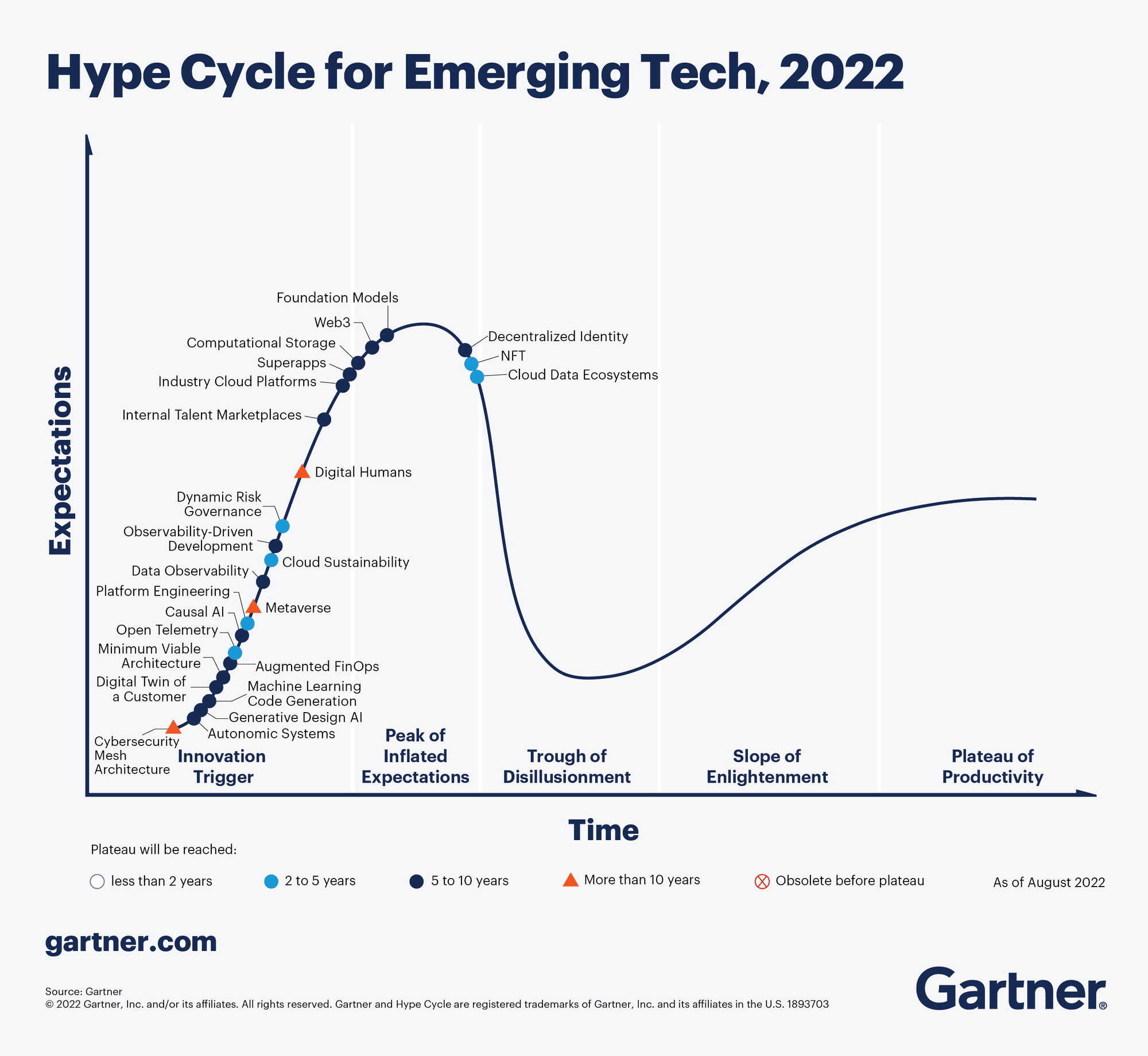
Image Source: https://www.gartner.com/en/articles/what-s-new-in-the-2022-gartner-hype-cycle-for-emerging-technologies
Looking at the latest wallet products, we can easily identify some obvious common development trends:
The Integration of Identity Wallets and Digital Asset Wallets
So far, identity wallets and digital asset wallets are still two different products, but the trend towards integration is becoming very evident. In addition to seeing a complete combination of DID digital identity and blockchain digital asset wallets in the DID Wallet product, most wallet products responsible for digital identity still lack digital asset functionality. However, with the rapid increase in Web3 applications, driven by user needs, it is a natural trend for digital identity functions to be integrated into wallets.
So which has greater potential: the rapid integration of digital asset functionality into identity wallets or the inclusion of identity management in digital asset wallets? Our judgment leans towards the latter. Digital asset wallets have always prioritized security and privacy, and users have managed valuable assets with these wallets, while digital identity wallets have largely remained in the demonstration stage. Since DID technology is still in its early stages, merely providing digital identity functionality means that these needs do not yet exist. For digital asset wallets, embracing market trends and adding DID support on the original basis will be relatively easier. We have reason to believe that within the next three to five years, support for digital identity will become a basic function of every digital asset wallet.
A More User-Friendly Experience Compatible with Traditional Internet Users, Allowing More Incremental Users to Enter Web3
Using password-free wallets to connect to applications has become a trend among existing crypto users and Web3 users, even being considered one of the features that distinguish Web3 from past Web2. However, it is undeniable that cryptocurrency and Web3 still represent just the tip of the iceberg compared to the vast number of internet users, and changing user habits is very challenging. Therefore, we predict that in the future, to attract more incremental users to Web3, a new, more user-friendly wallet experience that aligns with user habits will likely emerge. This will allow Web3 to truly become mainstream.
We believe that technology and user habits will not regress; the advanced Web3 features of user-controlled identities and ownership of their identity data and assets will not disappear. However, it is possible that a design will emerge that accommodates traditional user passwords without sacrificing decentralization. The first wallet to launch such a new user experience may achieve rapid user growth and become the future leader.
Wallets are Becoming Showcases for NFTs and Social Interactions
Starting with Rainbow Wallet, many wallets now feature vibrant designs that have won user favor. Wallet products have shed their past dull and rigid image, becoming rich and lively. Wallet products have transitioned from being purely tools to becoming entry points for users to understand and even showcase their assets. With the rise of more decentralized applications and SocialFi applications enabled by DID, wallets will also become the starting point for users to engage in new social activities.
Image Source: https://nft4metaverse.medium.com/rainbow-wallet-the-most-beautiful-ethereum-wallet-to-showcase-nfts-todays-pick-cc50dd1460ae
The trend of wallets having rich and user-friendly interfaces presents a significant opportunity to expose more users to wallet products, which is crucial for the development of the entire industry.
Better Security Mechanisms Allow Non-Technical Users to Ensure Asset Security
Future digital wallets will have better security, allowing users without technical backgrounds or extensive knowledge of concepts and blockchain to ensure the security of their identities, data, and digital assets with the help of wallets. We predict that wallet products will play an important role in this aspect, potentially becoming not only tools for managing users' identities, certificates, private keys, and assets but also important verification tools, user guides, and security gatekeepers.
In the past, wallets primarily served as tools, merely parsing blockchain protocols, allowing users to confirm and use their private keys for signing. However, this security relied on the users' own awareness and knowledge of security. In the future, the new generation of wallets may become independent security advisors and expert systems for each user, proactively helping users identify risks in transactions, automatically verifying information from all parties involved in transactions, and guiding users to make correct judgments. In this scenario, a decentralized wallet that fully stands on the user's side will become the best security guide for users navigating the Web3 space, ensuring that users without any technical background can secure their assets.
Integration of Wallets with DeFi and Decentralized Exchanges
A current trend is that wallets are increasingly integrating DeFi protocols deeply, even providing native interfaces for commonly used DeFi applications, enhancing user experience while increasing the competitiveness of wallet products. According to data released by MetaMask in July 2022, its monthly active users reached 30 million in 2022. Reports indicate that due to the demand for decentralized trading from these active users, MetaMask's revenue exceeded $250 million in 2021.
The integration of wallets with DeFi, cross-chain bridges, and decentralized exchanges can provide users with better experiences and reduce risks associated with user errors. The new generation of cross-chain bridges and DeFi centered around wallets has the opportunity to leverage the security prompts and verification capabilities that wallets provide to enhance system security in the future.
Support for Account Abstraction in New Generation Blockchains, Enhanced Security through Multi-Party Computation, and Improved Key Recovery Mechanisms
With the new generation of blockchains offering better support for account abstraction, wallets will also synchronize to support various features brought by account abstraction. Unlike the limitations of current wallets that implement account abstraction through smart contracts, the new generation of chains will provide better support for account abstraction. Once standards and norms are established, wallets will be able to offer users better and more secure experiences.
Additionally, advancements in multi-party secure computation technology may fundamentally change the architecture of wallets. The new generation of wallets may standardly support multi-party secure computation. Users may not need to worry about losing their keys while ensuring the security of their private keys, thus combining the advantages of custodial and non-custodial wallets.
Becoming a Hub for Decentralized Cross-Chain Interactions, Forming a New DApp Application Architecture
Cross-chain interactions have always been a key architecture with significant demand but also great difficulty. We now fully recognize that the future world cannot be satisfied by just one or a few public chains; rather, it will be a complex web structure. Therefore, how to achieve cross-chain interactions will be an important topic. For a long time, the industry has regarded "cross-chain bridges" as the solution, but immature cross-chain bridge technologies have led to multiple security incidents over the past year, resulting in cumulative losses of hundreds of millions. The new generation of wallet technology may provide a new approach to cross-chain interactions, treating each user wallet as a cross-chain node to complete business interactions across multiple chains. Of course, this cross-chain business cannot be achieved solely through wallets; it requires coordination among chains, cross-chain bridges, and various service nodes. Wallets themselves connect multiple chains and applications, and with a massive user base, assisting cross-chain interactions through wallets can further enhance the decentralization of the system, simplify the system architecture, and improve overall system security.
Implementing cross-chain architecture through wallets may even give rise to a brand new decentralized application architecture model. This application model may form a universal DApp architecture that supports cross-chain interactions, meaning that future DApps will generally support multiple blockchains and achieve cross-chain functionality at the application level.
Wallets may merge with new generation browsers that natively support blockchains and DApps.
Some say that wallets are like the browsers of the Web3 era. So what form will the most successful product of the internet era, the "browser," evolve into in the Web3 era? Will wallets replace browsers in the Web3 era? Our prediction is that this will not happen, but it is highly likely that the new generation of wallets and browsers will merge, or wallets may simply become a foundational functional module of the new generation of browsers. Meanwhile, hardware and mobile independent wallets will still exist but will be more closely integrated with the new generation of browsers, or the wallet module within browsers may likely be a continuation of independent wallets managed uniformly.
The decentralized applications of Web3 have also posed new demands on browsers. In the past two years, numerous new browser startups have emerged, not only improving user experience but also better supporting blockchain. We believe that the new generation of browsers and wallets will definitely be in a state of integration, potentially forming new product forms.