As the Federal Reserve continues to raise interest rates and reduce its balance sheet, liquidity in the cryptocurrency market is steadily decreasing, and market activity remains sluggish, entering a bear market. The remaining "liquidity" in the market, which is essentially our wallets, has become a target for scammers. The crypto world is a dark forest; while Crypto brings property ownership, it also means that once property is lost or private keys are leaked, there are almost no legal avenues or methods to recover it.
Why write this article?
Because Spinach's wallet was stolen, and the assets were almost completely looted. Ironically, as someone who has written popular science articles about wallet security, I also fell victim.
Although I lost a wallet that I had accompanied for a long time and its internal assets, after experiencing this incident, Spinach truly felt the warmth of the community and received much care and help from many "family members." With the help of a community member, I even managed to rescue nearly 30 NFTs that had miraculously survived from the hacker (not the NFTs that had already been stolen). Although the lost assets cannot be recovered, there are many experiences from this "Spinach wallet theft incident" that can be shared, and I hope this article can provide a victim's case to the industry and ring the alarm for other friends to prevent such "tragedies" from happening again.
The full text is 4,400 words, with an estimated reading time of 11 minutes.
Article Overview👀:
01/ How was my wallet stolen?
02/ How did the hacker obtain my private key?
03/ How did I rescue the NFTs from the hacker?
04/ How to complete all operations in the same block?
05/ What is MEV? What impact does MEV have on Ethereum?
06/ Final thoughts
How was my wallet stolen?#
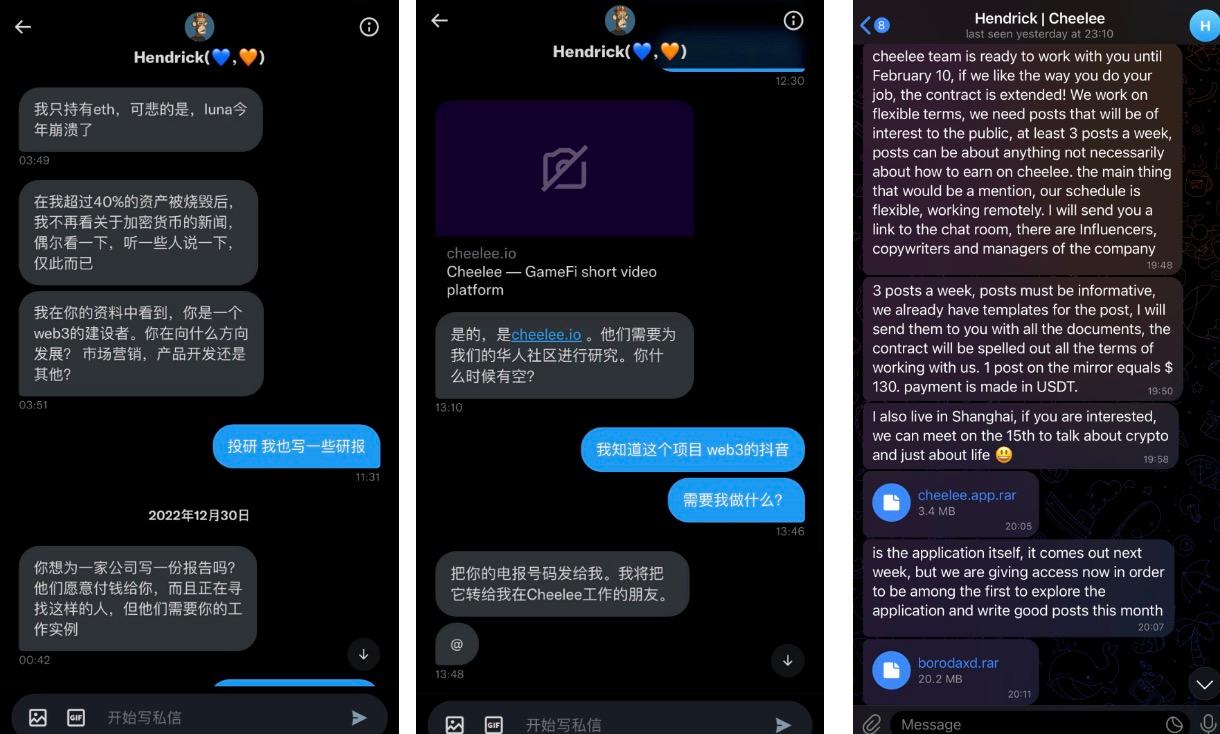
One day, someone messaged me on Twitter. At first, I didn't raise my guard because the scammer's Twitter account looked like a normal user. It started with some casual chatting, and then he began asking if I would be willing to create content for the Cheelee project and pay me for it, requesting some of my works for verification. So, I gave him my Telegram, and then he sent me some details about how to create content and two files on Telegram. After downloading and clicking the files, nothing happened, which made me realize something was wrong. I then opened my MetaMask to check, and unsurprisingly, the wallet was stolen, all assets were taken, and the NFTs were directly sold for offers and converted to ETH. (I can only say that Spinach was careless in trying to make some extra money; in fact, one should be cautious when a stranger sends files on Telegram).
How did the hacker obtain my private key?#
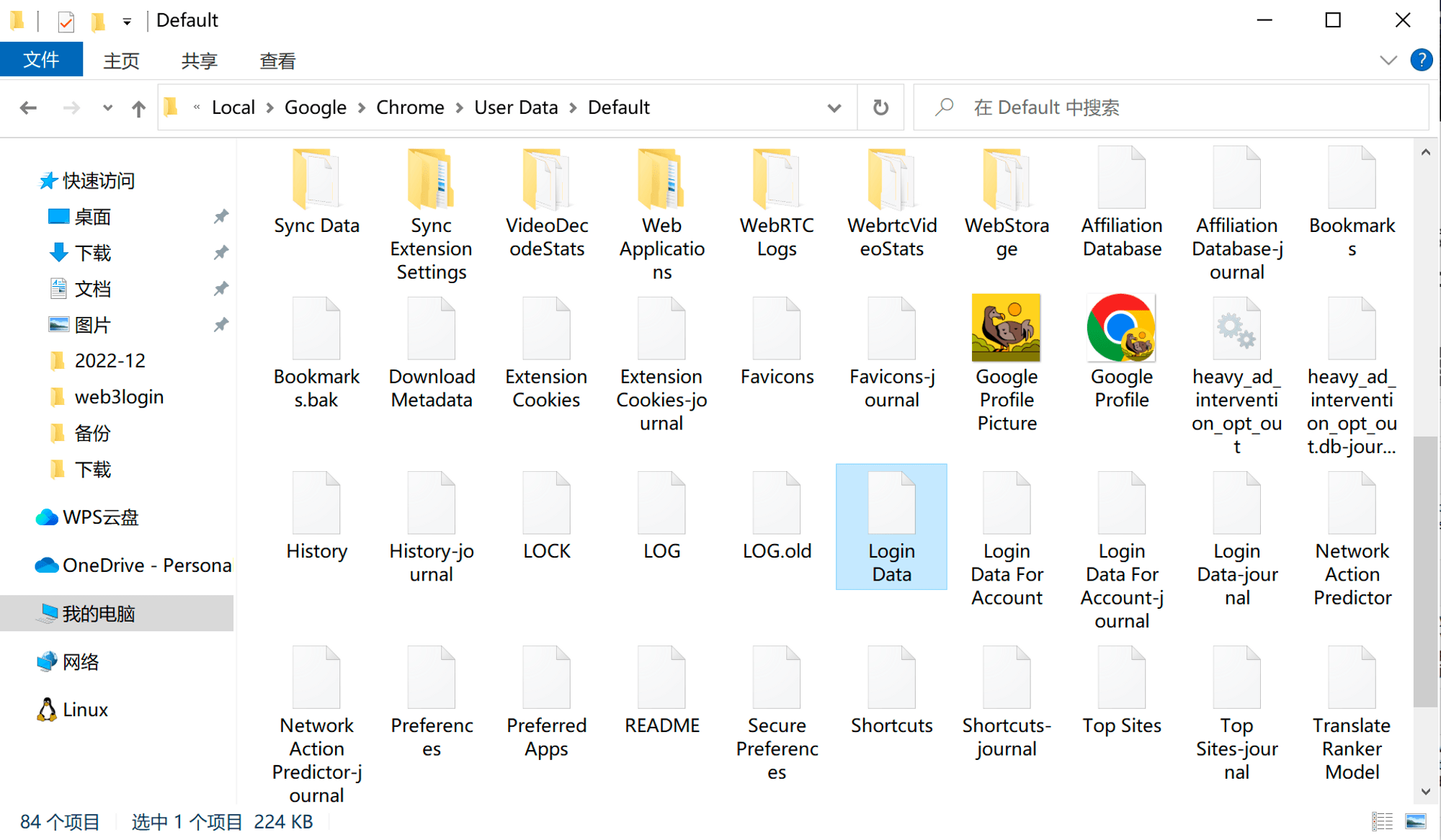
My private key was encrypted and stored in the MetaMask extension in Chrome. How did the hacker get my private key? This starts with the Chrome browser: can you imagine? This browser, which holds a 66% market share globally, has a huge security vulnerability! What is this vulnerability? If you open the Default folder of your Chrome browser at the path shown in the image below, you will find a file called Login Data, which stores every password you have saved in Chrome. However, if you try to open it directly to read it, you will find it unreadable, displaying a bunch of garbled text, because this file is encrypted with the AES algorithm, and brute-forcing it would take an eternity. So, the passwords you save in Chrome are actually very secure, but where is the problem?
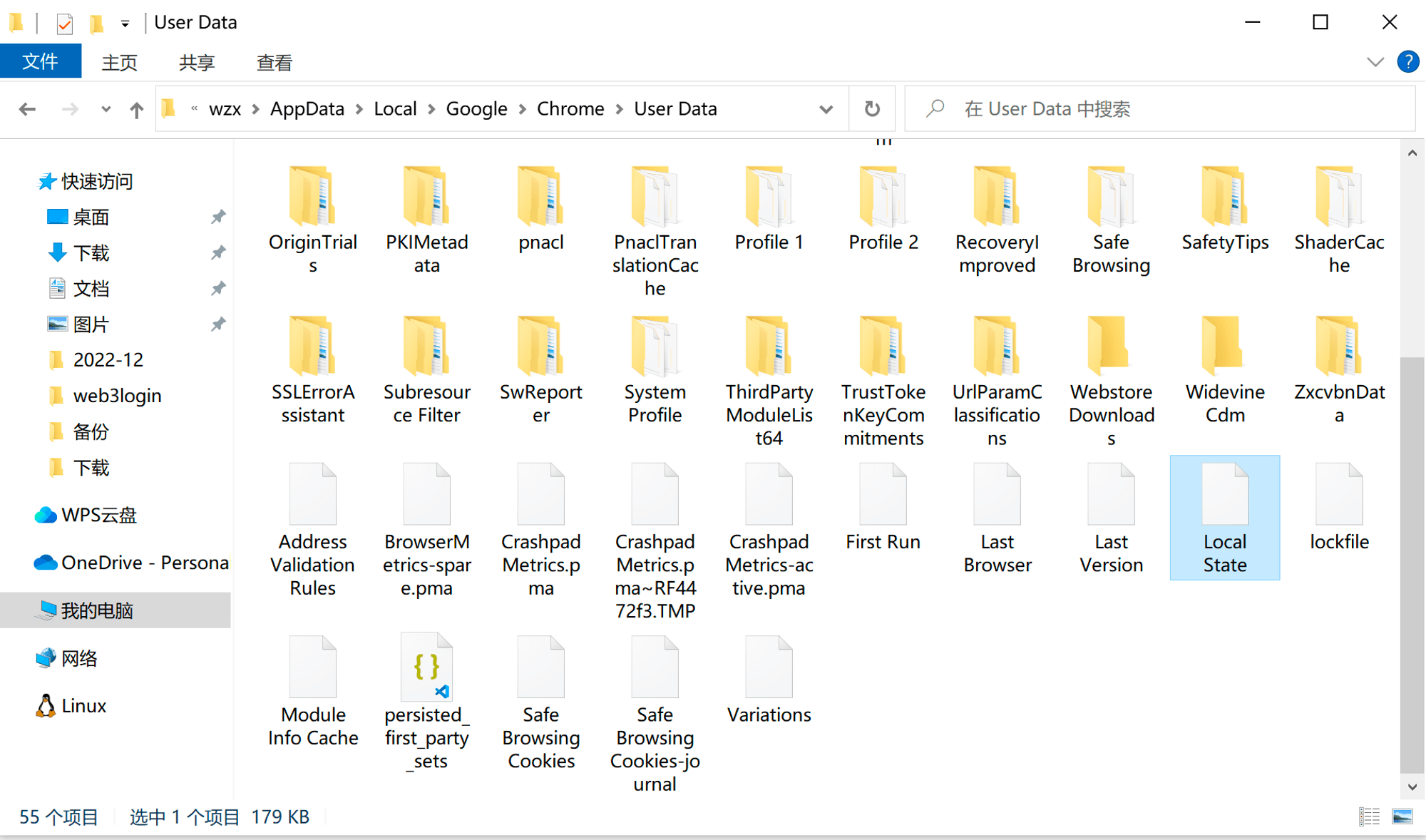
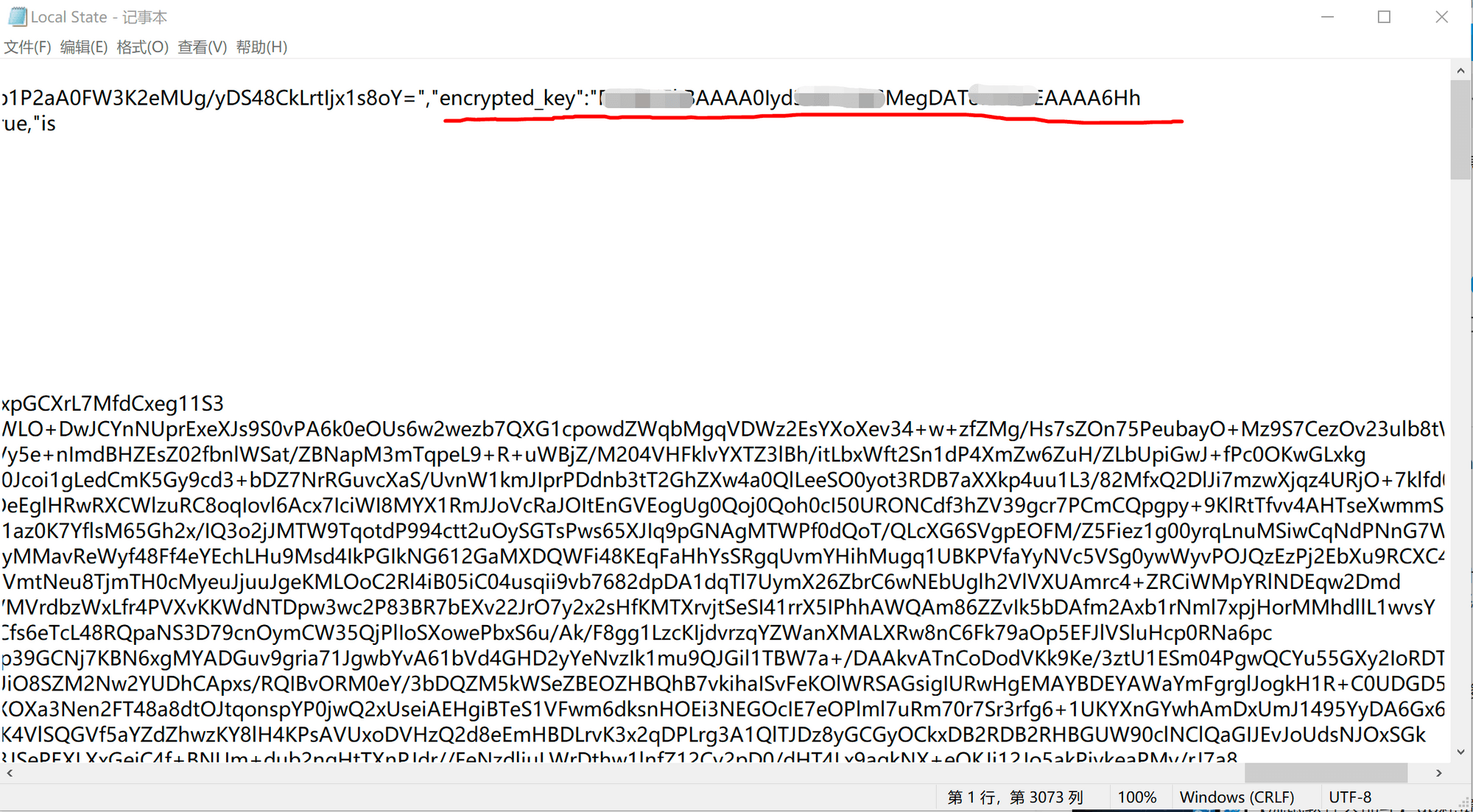
If you go back one directory in User Data, you will find a file called Local State. If you open it and search for "encrypted," you will find a string of keys. What is this key? It is the key string needed to decrypt the Login Data AES algorithm, which would take hundreds of years to brute-force!!! This is outrageous! What does this mean?
It means you made an unbreakable safe out of the strongest material in the world to store your passwords, but you left the key to the safe right next to it. When a thief comes in, they just take the key and open the safe! Moreover, this key string is generated by the Windows system's password generation tool and is uniquely bound to the generated computer ID, meaning that encryption and decryption can only be performed on this computer. Chrome has stored the decryption key string in plain text locally, so the hacker only needs to take the key string to decrypt and obtain all my passwords.
The password for MetaMask is not stored in Chrome's password file. So why did my private key leak? Because the password I used for MetaMask was the same as my habitual password, once the hacker obtained my habitual password, entering MetaMask was just a matter of minutes, and thus, my private key was leaked. Not only that, but all accounts stored in the Chrome browser were leaked, and even my Twitter and Google accounts were frozen.
How did I rescue the NFTs from the hacker?#
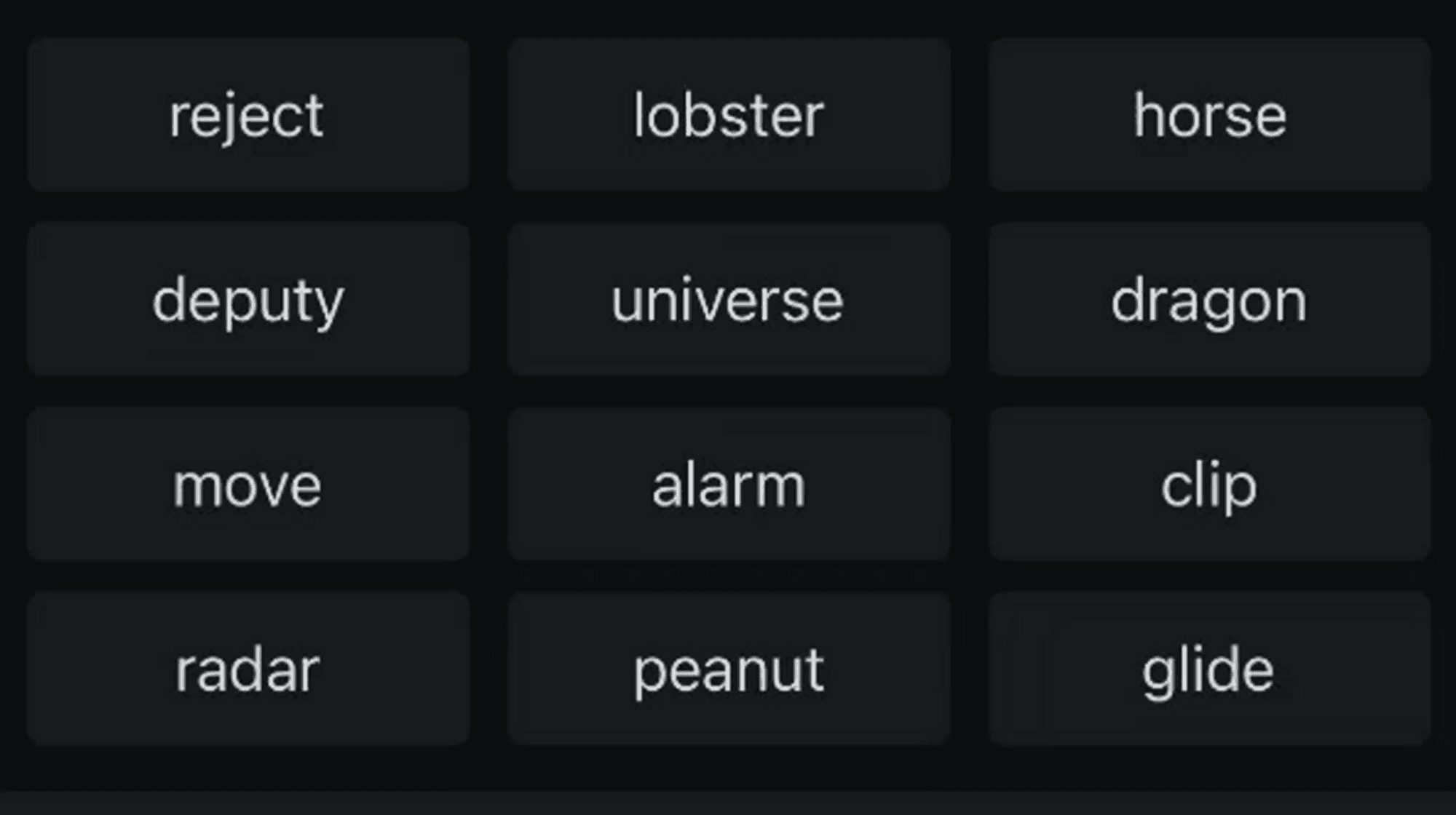
After my wallet was stolen, the hacker sold all NFTs with offers on OpenSea and transferred all the funds away. Fortunately, some NFTs survived, including an ENS and some NFTs without offers, but one newly minted DeBox little snake was not sold. Perhaps due to some bugs on OpenSea, this NFT was transferred from another white list address I had minted, and for some unknown reason, it was not displayed, allowing it to escape disaster. So when I tried to transfer gas into my wallet, I found that my wallet was under a "cleaner attack," which can also be called a gas-sniping robot; the gas fee I transferred in was instantly taken away!
What is a gas-sniping robot? It is a robot that immediately detects when you transfer gas into your wallet and instantly transfers it away. These robots are usually active in wallets with leaked private keys. This robot is also active in a scam that deliberately leaks private keys, where scammers will intentionally leak the private key of a wallet containing USDT, but this USDT is blacklisted by the contract and cannot be transferred. The scammers are targeting the gas you attempt to transfer in. The following image is an example (on the Tron chain); interested friends can take a look, but don't transfer gas into it!
Once my wallet was targeted by the gas-sniping robot, it meant I could not transfer my surviving NFTs because I had no way to transfer gas into the wallet to pay for the operation to transfer the NFTs away. Was my NFT to be forever trapped in the wallet? Just when I was at my wit's end, the power of the community came through, a member of the Buidler DAO community stepped up to help me rescue the surviving NFTs from the gas-sniping robot!
There is true love and kindness in the world!!!
So how did this community member do it?
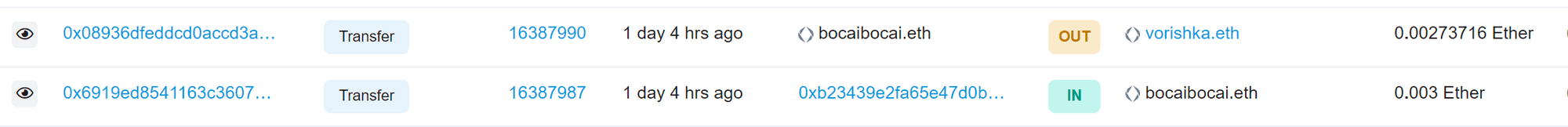
First, let’s see how fast I would need to act manually to transfer my NFTs away before the gas-sniping robot. In the blockchain explorer, you can see that when I transferred in the gas fee (block height 16387987), the gas-sniping robot transferred all the gas away three blocks later (block height 16387990). In Ethereum's proof-of-stake mechanism after the merge, the block time is fixed at 12 seconds per block, so does this mean I just need to operate within the first two blocks (within 24 seconds) to outpace the robot? This thought is too naive; if it were that slow, it wouldn't even be called a robot.
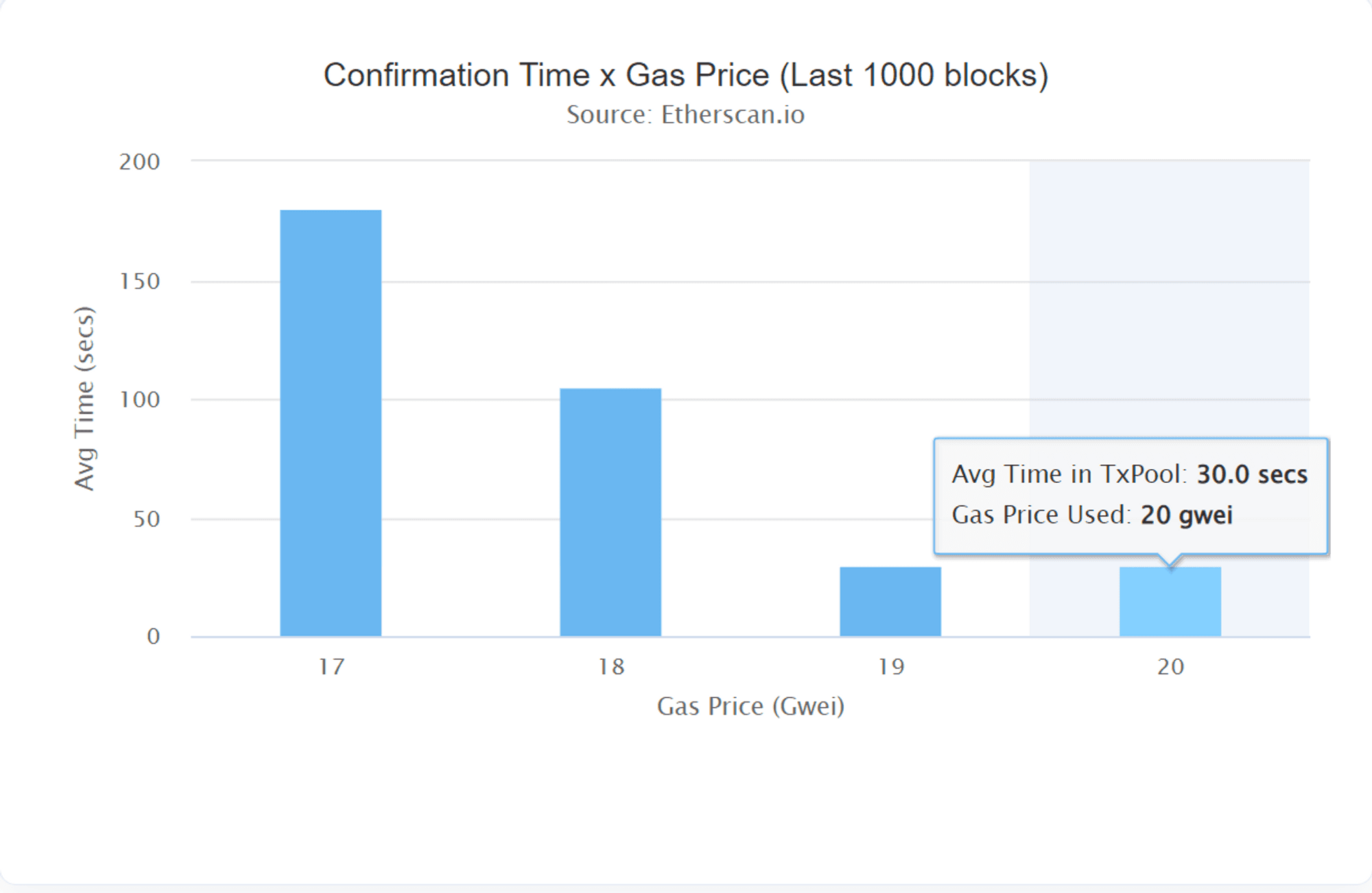
In Ethereum, the processing speed of a transaction depends on how much gas fee you pay. If you want your transaction to be processed faster, you need to pay more gas fees. The average gas fee fluctuates with Ethereum's transaction demand. Under normal circumstances, processing a transaction takes about 30 seconds, which means if I want to rescue the NFT before the gas-sniping robot takes the gas, I need to complete my operation within 36-30=6 seconds, which is nearly impossible because even if I act immediately after seeing the gas arrive, the time it takes for MetaMask to pop up the interface is already about 6 seconds. So how can I transfer the NFT before the gas robot takes the gas?
The answer is to complete the transfer of gas into the wallet and the transfer of the NFT in the same block, so the robot cannot take the gas away because it needs to continuously monitor the blockchain explorer to confirm if gas has been transferred into the wallet. If all operations are completed in one block, even if the robot detects the block, I have already transferred the NFT away and left no extra gas for the robot to take.
How to achieve all operations in the same block?
This requires using the Flashbots searcher-sponsored-tx feature, which is mostly used in wallets monitored by robots due to leaked private keys.
Tech-savvy friends can check it directly on GitHub:
Github Repo not found
The embedded github repo could not be found…
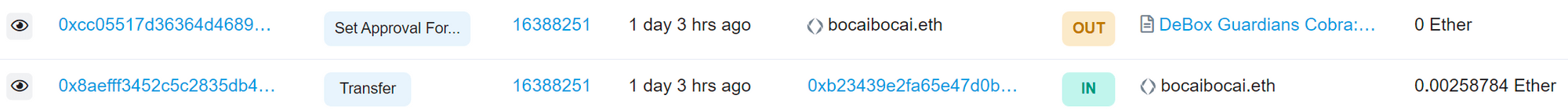
This feature of Flashbots supports transferring gas from one wallet to another while also including a transaction, thus completing all operations in the same block. In the blockchain explorer, you can see that the gas transfer and contract call were completed in block 16388251.
By the way, what is Flashbots? Flashbots is a research organization composed of blockchain researchers, builders, and white hats focused on mitigating the negative externalities of Maximal Extractable Value (MEV) on stateful blockchains (like Ethereum).
What is MEV?
What impact does MEV have on Ethereum?
Maximal Extractable Value (MEV) refers to the maximum value that can be extracted from block production beyond the standard block rewards and gas fees by adding, excluding, and changing the order of transactions in a block. How to understand this? For example, we first need to know that in Ethereum, once a transaction is initiated, it will be placed in the mempool (a pool of pending transactions) waiting to be packaged by miners. Miners can see all transactions in the mempool, and they have significant power; they control the inclusion, exclusion, and order of transactions. If someone bribes miners by paying more gas fees to adjust the order of transactions in the pool for profit, this is considered a form of MEV.
You might be wondering how miners can profit by changing the order of transactions?
One MEV technique is called "sandwich attack," where this method of extracting MEV involves monitoring large DEX transactions on-chain. For example, if someone wants to buy $1 million worth of a token on Uniswap, this transaction will significantly raise the token's price. When this transaction is placed in the mempool, monitoring bots can detect it. At this point, the bot can bribe the miner packaging the block to insert a buy operation for this token ahead of the person, and then after the person's purchase, execute a sell operation, effectively sandwiching the large DEX trader in between. This way, the person initiating the "sandwich attack" profits from the price increase caused by the large transaction, while the large trader incurs a loss.
In addition, other methods of obtaining MEV include DEX arbitrage, liquidation bots, etc. The existence of MEV has consistently brought negative impacts to Ethereum, such as the losses and poorer user experience caused by "sandwich attacks," network congestion and high gas fees due to frontrunning competition, and even threatening the integrity of the blockchain to some extent. As of January 2023, profits from MEV have reached $680 million.
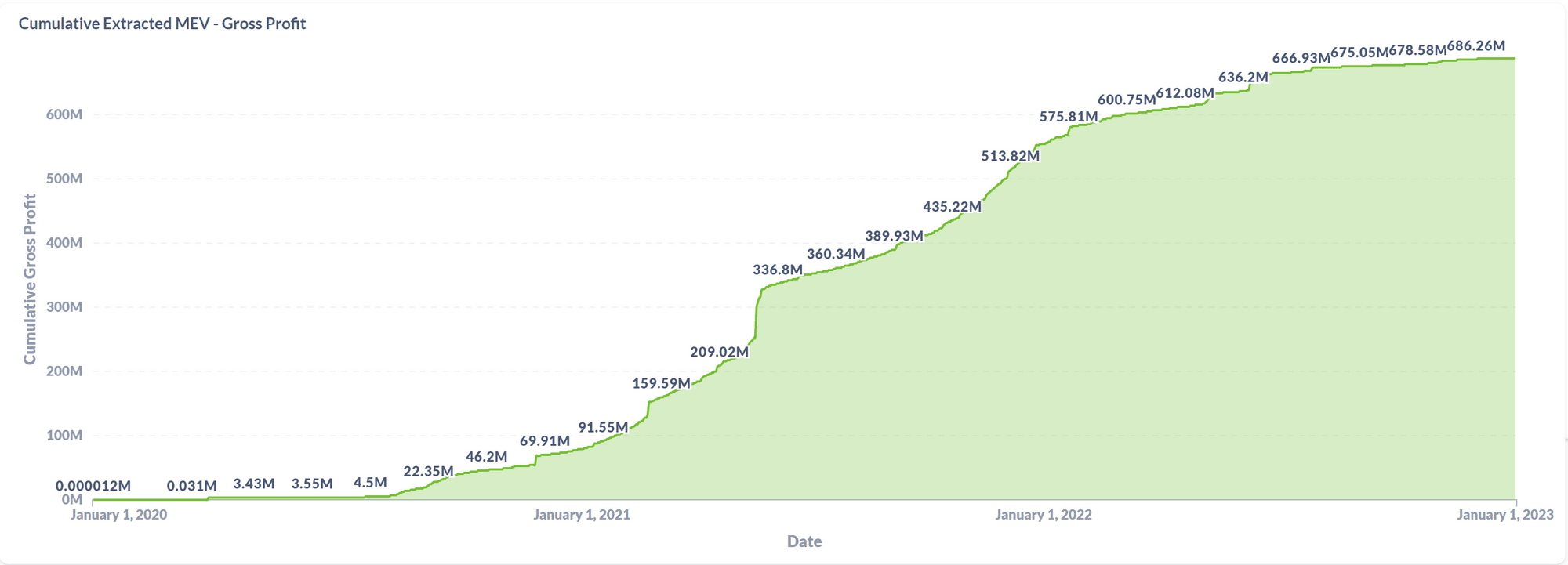
Data source: https://explore.flashbots.net/
The emergence of Flashbots has shed light on the dark forest of MEV. Flashbots has conducted extensive research on MEV and developed several products that have mitigated the negative impacts of MEV on Ethereum to some extent. Although Flashbots cannot solve the problems caused by MEV, Ethereum has proposed a new mechanism to address MEV issues in its new sharding plan, Danksharding (a preview of which will be the topic of my next article). If you are interested in Flashbots and MEV, you can check the following links.
Official Ethereum introduction to MEV
https://ethereum.org/zh/developers/docs/mev/#mev-extraction-flashbots
Official website of Flashbots
Is there anything else you want to say?
After my wallet was stolen and seeing all my crypto assets and favorite NFTs gone, I felt very upset, especially since my favorite DeBox family was lost. I am grateful to the community members who stayed with me, offering advice and support after learning about my situation. Even after rescuing the NFTs, the DeBox project team airdropped an NFT to me as a consolation; DeBox is truly a warm team, and I am a huge fan!
Regarding wallet security, one must not be careless. Before this, I never thought I would become one of the victims. As the article was nearing publication, I saw that a KOL, NFT GOD, also fell victim to a hacker attack and lost all assets, with all social accounts leaked and used to send scam messages. The reason was downloading fake software from a Google ad link, similar to the previous fake TP wallet scam. Therefore, never download any files from strangers, and always verify if the software is from the official website before downloading.
In addition, do not keep all your crypto assets in a hot wallet; storing assets in a cold wallet is definitely the safest option. It is also best not to use habitual passwords for your MetaMask password because the MetaMask extension on Chrome is not absolutely secure. It is essential to learn about wallet security.
If you, too, have encountered a situation like Spinach, where your wallet was stolen but some NFTs that may hold significance for you survived, yet your wallet is being targeted by gas-sniping robots, you can reach out to and message the community member who helped me rescue my NFTs for assistance @Tom16013Tom1601. Don't forget to offer some compensation for their help!